AMI is a network processing system to measure, gather, store, analyze and utilize user's electricity information. It is a critical part of Smart Grid[1] and also the pointcut to promote the construction of smart grid[2]. However, the stable and reliable data transmission link is the foundation to implement AMI successfully. ZigBee has a strong anti-interference ability, low cost, low power consumption, short time delay, reliable transmission and large network capacity[3], which makes it a widespread application in AMI. It has become the principal way of short distance wireless communication in AMI, especially in the wireless meter reading[4] and Home Area Network(HAN)[5]. There is no lack of the researches on ZigBee application in the smart grid at home and abroad[6-7]. The National Institute of Standards and Technology (NIST) recommended ZigBee as one communication standard in the smart grid interoperability standards established in 2010[8].
The advantages of ZigBee applied in AMI can be reducing cabling, decreasing costs, easy maintenance, etc. This also greatly increases the security threats to the grid because of the available access points and the access path provided by wireless channel. Therefore, the security of ZigBee communication applied in AMI is a critical issue. In Ref.[9], the importance of key management has been pointed out, but there is not any specific scheme proposed. Several key management schemes of WSNs based on key predistribution were proposed in Refs.[10]-[12], however, these solutions are lack of node authentication mechanism, and if the captured nodes reach a certain number, the key will be revealed quite easily, so the system will be insecure. In Ref.[13], an elliptic curve based hierarchical cluster key management scheme in WSNs was proposed, though it can guard against different types of attacks, the consumption of resources in computing and storage is still redundant. The key management schemes of WSNs based on ECC proposed in Refs.[14] and [15] can realize the node authentication and improve the security of the whole network. However, these schemes did not consider the system structure, message transmission patterns and security requirement of AMI. So, those key managements are not allowed to be applied directly to an AMI system. In Ref.[16], a hierarchical access control key management method based on ECC scheme was proposed for the electric vehicles to join the smart grid. Which solved the access control in the user layer, the exchange of keys in this method was realized based on the partial order of each safety class in the hierarchical system, so once a safety class was added or deleted, the partial order and consequently the key changes with it. Therefore the update and recycle of keys are rather inconvenient in this method. In Ref.[17], an intelligent agent security communication model in smart substation based ECC was proposed, in which the ECDH and ECDSA were effectively improved to complete the negotiation of keys and the identification. Nevertheless, this method only works for the exchange of keys in a peer-to-peer communication system, which is not the case of an AMI system. Plus, the consumption of resources in computing and storage is beyond the capacity of a ZigBee node. In Ref.[18], a key management scheme was proposed according to the different message characteristics in AMI, which effectively solves the problem of complicated information transmission in AMI system. However, there are potential security risks in the initial user key distribution and the storage of key is too enormous for ZigBee node.
The above analysis demonstrates the prospective of ECC's application in the smart grid and WSNs. However, there are such drawbacks in above schemes, so we propose a key management scheme of ZigBee based on Elliptic Curve Cypher (ECC), which is suitable for AMI according to the message transmission patterns mentioned in Ref.[16] .The advantages of the proposed scheme include: the key store consumption is greatly reduced; the security of the key distribution during ZigBee communication is improved.
2 AMI System Structure and Security Requirements 2.1 AMI OverviewAMI is an integrated solution of multitudinous technology and application, and mainly includes 4 components:Smart Meter (SM), communication network, Measurement Data Management System (MDMS) and Home Area Network (HAN)[19].
SM is installed in the user side, and its biggest difference from the ordinary electric meters is that smart meters have built-in communication modules, by which smart meters can exchange information with MDMS[20]. HAN has been brought up in recent years, which embodies the interaction between power grid and the user. Smart meters and smart electrical equipment are connected in HAN, and the user can control the equipment preferably according to the power grid operation state and electricity price obtained at any time. Therefore, AMI provides the platform and technical support to the interactivity between users and power grid.
2.2 AMI Communication ArchitectureAMI communication architecture includes three layers: wide area network (WAN), local area network (LAN) and HAN [21].
WAN is a network that provides connectivity from data concentrators to MAMS in the utility center, which also has a protocol system, and this network requires long communication distance, high bandwidth and very high real-time demand.
LAN is the network of neighboring smart meters that communicate with data concentrators, which also has a protocol system, and the characteristic of this network is that the communication distance is around 20-500 m, the bandwidth is medium and the real-time demand is not high.
HAN is the communication of the network between smart electronic appliances at customer premises and SMs in residential and industrial areas, and the characteristic of this network is that the communication distance is short, the bandwidth is low and the real-time demand is not high.
The common communication modes at all layers are shown in Table 1, from which we can see ZigBee can be applied in HAN and LAN.
| Table 1 Common communication mode in AMI |
2.3 AMI Communication Security Requirements
AMI should meet the security requirements which are pointed out in IEC62351, mainly include four aspects, such as confidentiality, integrity, availability and non-repudiation[22].
Confidentiality is to make sure the information cannot be obtained by unauthorized users, which is usually realized by cryptography. In AMI, the information that needs to ensure confidential includes:customers do not like unauthorized people and companies to know about their metering data or usage patterns; operators also want their operation data to be a secret from the market. So, there must be proper encryption mechanism in ZigBee communication of AMI.
Confidentiality can guarantee data not to be leaked, and integrity can guarantee data against tampering and breaking by unauthorized users during transmission. WSNs collect all kinds of data and instructions in the grid, which will produce major safety accidents and serious adverse effects once been tampered and damaged.
Availability ensures authorized users to use the information timely and reliably.
Non-repudiation in AMI systems means preventing deny behaviors that have already occurred or pretend behaviors that did not happen before.
The security schemes involved in AMI mainly include:communication data security, authentication management, access control, risk defense, intrusion detection and communication device security[23].Since the key management is the basis of meeting the needs of confidentiality and integrity[24], this paper mainly analyzes the ZigBee communication key management scheme.
3 Application and Message Transmission Patterns of ZigBee in AMI 3.1 Application of ZigBee in AMIAfter accomplishing the smart home series standard, ZigBee alliance focuses on AMI as the most important application area, and then finishes drafting all relevant documents of the AMI applications, and issues ZigBee Smart Energy Profile [25]. This profile stipulates the process of the start of the device (such as smart meter or concentrator) with ZigBee, the process of a device searching and joining a network, and the process of device address allocating and managing, which provides the technical basis for ZigBee applied in HAN and Wireless Meter Reading.
Fig. 1 shows an example of ZigBee applied in AMI, the collector node (CN) plays the role of repeater, which is equal to the cluster head in the ZigBee network. The functions of the collector node include: receiving metering data from SMs and sending control instructions to intellectual electric apparatus by RS-485, PLC and ZigBee communication technology; sending metering data to sink node (SN) by ZigBee technology, which equals to the data concentrator introduced in Section 2.2. The functions of the SN include: converging and storing the data from CN; sending the data to MDMS after being simple processed. Therefore the SN's role is equal to ZigBee coordinator in the network.
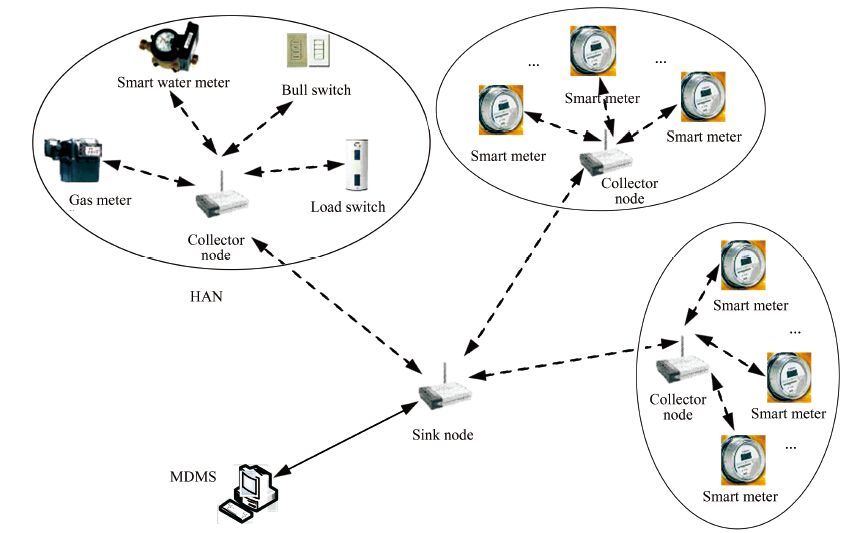
|
Figure 1 AMI system diagram based on ZigBee |
3.2 Message Transmission Patterns of ZigBee in AMI
There are various interactive information transmitted by ZigBee, such as metering data, illegal electricity utilization detection information, electricity price information and remote control information.The transmission mode of the information can be categorized as unicast communication and multicast communication[18], and the sender, receiver, and transmission mode for each message type are listed in Table 2. Unicast communication mode means messages are transmitted from one point to another one, e.g., a message is transmitted from CN to SN;multicast communication mode means message are transmitted from one point to some other points simultaneously, e.g., a message is transmitted from SN to some CNs.
| Table 2 Message transmission patterns of ZigBee in AMI |
In this paper, we propose a key management scheme which can effectively support both ZigBee message transmission patterns in AMI, and can satisfy the demands of the transmission time of each message.The proposed scheme includes two aspects:key management for unicast communication and multicast communication, so we can select the corresponding key management scheme according to the message transmission way.
4 Key Management of ZigBee Based on ECC 4.1 Public Key and Private Key EstablishmentThe data encryption algorithms stated in IEC 62351includes DES, AES, RSA, ECC, etc.[26], and ECC has a low resource consumption and shorter key length compared to other public key algorithms under the same security strength. In AMI, smart meters and CNs both have a limited memory, so ECC can both meet the security needs of AMI and compensate for the realistic condition of limited memory of the node. The proposed key management scheme is realized through ECC, which is based on the ECC public key and private key of SN, CN and SM. The details of establishment are as follows:
1) Selecting an elliptic curve in prime fields.
The elliptic curve selected in this paper is defined in prime fields GF(p), denoted by Ep(a, b), and the equation of the curve is:
| $${y^2} = {x^3} + ax + b\left( {{\rm{mod }}p} \right)$$ | (1) |
Where, x, y∈GF(p); a, b∈GF(p); p is a prime and greater than 3; a, b should meet Eq. (2):
| $$4{a^3} + 27{b^2} \ne 0\left( {{\rm{mod }}p} \right)$$ | (2) |
And the choice of the p is decided by the number n of network nodes, in general, p and n must satisfy the formula: p > n.
2) Calculating the points on the elliptic curve.
Firstly, to select a random number xi∈GF(p) when calculating the points on the elliptic curve;then, to calculate yi according to Eq.(1), and if yi∈GF(p), xi, yi is the point on curve Epa, b.After calculating all the points, select a point P as base point whose order is large enough, and assign it to each SN, CN and SM.
3) Getting the public key and private key of each node.
In this paper, the public key of sink node C is denoted as QC, and the private key is denoted as dC; the public key of ith collector node Si is denoted as QSi, and the private key is denoted as dSi; the public key of jth smart meter QSij which is subject to ith collector node is denoted as QSij, and the private key is denoted as dSij. If the order of the base point P is m, every private key can be a positive integer selected randomly from [1, m-1], and the public key is the scalar multiplication product of private key and base point. Public keys such as QC, QSi and QSij are the points on the elliptic curve, and they can be realized by point adding algorithm. Eqs. (3) and (4) are as follows. The sink node stores all the public keys, and allocates the corresponding public key to both parties of unicast communication and multicast communication.
| $$\left\{ {\matrix{ {{x^3} = {{\rm{\lambda }}^{\rm{2}}} - {x_1} - {x_2}} \cr {{y^3} = {\rm{\lambda }}\left( {{x_1} - {x_3}} \right) - {y_1}} \cr } } \right.$$ | (3) |
where (x1, y1) is the coordinate value of given point M; (x2, y2) is the coordinate value of given point N; (x3, y3) is the coordinate value of M+N; the value of λ can be acquired by Eq. (4):
| $$\left\{ {\matrix{ {{\rm{\lambda = }}{{{y_2} - {y_1}} \over {{x_2} - {x_1}}}, } & {M \ne N} \cr {{\rm{\lambda = }}{{3x_1^2 + a} \over {2{y_1}}}, } & {M = N} \cr } } \right.$$ | (4) |
The unicast communication is a basic communication mechanism of ZigBee, which is also an essential message transmission pattern in AMI, as shown in Table 2. The unicast communication in AMI includes the communication between collector nodes and smart meters and the communication between collector nodes and sink nodes so as to realize the transmission of some metering information and control information in AMI. The key used to encrypt the data transmitted in ZigBee unicast communication in AMI is called Link Key denoted as LK.
4.2.1 Link key generation and distributionIn this paper, the process of link key generation and distribution is illustrated through the unicast communication of collector node and sink node. The steps are as follows:
1) The LK establishment in the sender Si.
S1.1 The generation of LK additional materials:
| $$MacData = {H_1}\left( {{N_{Si}}, {d_{Si}}} \right)$$ | (5) |
where, H1( ) is a hash function;dSi is the private key of Si;NSi is a random number selected by Si.
S1.2 The generation of LK in Si:
| $$L{K_i} = {H_2}\left( {MacData, ID} \right)$$ | (6) |
where, H2( ) is another hash function;QSi is the public key of Si.
S1.3 The generation of authentication information in Si:
| $$Sig{n_i} = HMA{C_{LKi}}\left( {MacData, I{D_{si}}} \right)$$ | (7) |
where, HMACLKi is a MAC using hash function with an encryption key LKi; IDsi is the identifier of Si.
2) Sending the cipher text to sink node C.
| $$EMs{g_{{s_i} \to c}} = {E_{QC}}\left( {MacData\left\| {Sig{n_i}} \right.\left\| {I{D_{si}}} \right.} \right)$$ | (8) |
where, EQC( ) is an ECC encryption function with QC acted as its public key.
3) The LK establishment in the receiver sink node C.
S3.1 Decrypting the received message MsgSi→C from Si:
| $$Ms{g_{{s_i} \to c}} = D{E_{dC}}\left( {EMs{g_{{s_i} \to c}}} \right)$$ | (9) |
where DEdC( ) is an ECC decryption function with dC acted as its private key.
S3.2 The generation of LK in C:
| $$L{{K'}_i} = {H_2}\left( {MacData, {Q_{Si}}} \right)$$ | (10) |
S3.3 The generation of authentication information in C:
| $Sig{n'_i} = HMA{C_{L{{K'}_i}}}\left( {MacData, I{D_{si}}} \right)$ | (11) |
4) If Sign'i=Signi, LK'i=LKi and the Link key establishment is successful; and if not, the Link key establishment is failed.
4.2.2 Link key rekeyingIn AMI, there will always be some new collector nodes to join in the network or some compromised nodes to leave the network. When a new collector node joins in the network, the public/private key pair and unicast communication link key should be distributed to it, which can refer to Section 4.1 and Section 4.2.1.Because of the link key between sink node and collector node is independent, when some collector nodes leave network, we just need to delete the relevant nodes' key information from the sink node.
4.3 Key Management for Multicast CommunicationThe multicast communication based on ZigBee refers that the sink node communicates with multiple collector nodes simultaneously in AMI system, and the key that is used for data encryption in the communication is called network key denoted as NK.
4.3.1 Network key generation and distributionThe steps of key management of NK are as follows:
1) The NK establishment in the sender C.
S1.1 The generation of NK additional materials:
| $$MacData = {H_1}\left( {{N_C}, {d_C}} \right)$$ | (12) |
Wherewhere, dC is the private key of the sink node C;NC is a random number chosen by C.
S1.2 The generation of NK:
| $$NK = {H_2}\left( {MacData, {Q_C}} \right)$$ | (13) |
where QC is the public key of sink node C.
S1.3 The generation of authentication information in C:
| $$Sig{n_C} = HMA{C_{NK}}\left( {MacData, I{D_C}} \right)$$ | (14) |
where IDC is the identifier of C.
2) Sending the cipher text to Si.
| $$EMs{g_{C \to {S_i}}} = {E_{QSi}}\left( {MacData\left\| {Sig{n_C}} \right.\left\| {I{D_C}} \right.} \right)$$ | (15) |
3) The NK establishment in Si.
S3.1 The node Si decrypts EMsgC→Si according to the private key dSi:
| $$Ms{g_{C \to {S_i}}} = D{E_{dSi}}\left( {Ms{g_{C \to {S_i}}}} \right)$$ | (16) |
S3.2 The generation of NK in Si:
| $$NK' = {H_2}\left( {MacData, {Q_C}} \right)$$ | (17) |
S3.3 The generation of authentication information in Si:
| $$Sig{{n'}_C} = HMA{C_{NK'}}\left( {MacData, I{D_C}} \right)$$ | (18) |
4) If Sign′C=SignC, NK′=NK and the network key establishment is successful; and if not, the network key establishment is failed.
4.3.2 Network key rekeyingThe strategy of network key rekeying is different from link key rekeying;considering the network's forward security and backward security, the network keys must be re-established, no matter when new collector nodes join in the network, or collector nodes leave the network.In the process of NK rekeying, it is most important to alter the random number NC in Step S1.1 of Section 4.3.1, and the rest steps can refer to the procedures that are proposed in Section 4.1 and Section 4.3.1.
5 Performance AnalysisThe results obtained in this paper are based on the simulation (OMNeT++) of network model and mathematical analysis. Multiple scenarios and test cases according to the improved ZigBee-2007 specification have been tested to generate different values. In simulation, it is assumed that the energy of the nodes in network is fixed.The simulation parameters in the configure file (.ini file) are listed in Table 3.
| Table 3 Simulation parameters |
5.1 Security Analysis
In this paper, the security of proposed scheme is based on the elliptic curve discrete logarithm problem (ECDLP), which is described that it is difficult to obtain private key according to the public parameter set and public key in ECC.
Up to now, there is no effective way to crack ECDLP.Generally speaking, the time complexity is exponentially growing in ECDLP.So, the security of proposed scheme can be concluded based on ECDLP as follows:
1) This paper solves the problem of transmission security of the initial key and additional key material in Ref.[18].
In Ref.[18], the initial key and additional key material should be transmitted in a secret way, which is difficult to realize in software programming, and if realized by hardware (such as smart card), the cost will increase. In this paper, the ECC is used to avoid this problem, because the information needed to be transmitted in initial phase are only the base point P and the public key of every node, which can be transmitted in an open way.
2) It is difficult to crack the session key (including LK and NK) in this paper.
In the sending end, the establishment of both the link key and the network key needs to use the private key of sender.The session key established in the sender can not be cracked because of the difficult to acquire the private key. In the receiving end, the establishment of session key bases on MacData, which can be obtained through decrypting the received information with the private key of the receiving end. Because it is difficult to crack the private key of the receiving end, cracking the session key of the receiving end can also be very difficult.
3) The authentication process improves the security of key generation and distribution.
In this paper, the session keys are held successfully only if it passes the authentication. The authentication can detect the false identity attack effectively.Taking being under attack during link key establishing process as an example, if the sender is a fake identity node, it can not get the private key of original node, so it generates the new public key QSi'', new private key dSi'' and new random number N''Si, and then it works out the link key LK''i and authentication information Sign''i.However, in the receiving end, the sink node stores the public key QSi of original collector node, so the link key generated by the sink node is different from LK''i, and the authentication information is different too, which indicates that the link key establishment is failed.As above, the authentication in the process of network key establishment plays a similar role.
4) Forward and backward security.
In ZigBee unicast communication of AMI, there is a sole link key between the sink node and each collector node, so any captured collector node would not leak out any other node's information to the attacker except for its own.In ZigBee multicast communication of AMI, if there are any nodes that join or quit the network, the network key will be regenerated and refreshed.As a consequence, the forward and backward security can then be ensured in our scheme.
5) The ability to resist node capture.
If a node in the WSNs is captured, the enemy will get the key of the captured node, and even get the keys of other links.Therefore, the capture resistance ability of nodes is a very important indicator to judge security performance.It simulated with the software OMNeT++ and got the key captured ratio of other links when the number of captured nodes was 10, 20, 40, 60 and 100 separately. To reduce the errors, each experiment was conducted for five times and got their mean. Simulation results are shown in Fig. 2, with the number of captured nodes increasing, the capture resistance ability of the three schemes are decreasing gradually.Since ECC is used in our scheme and the scheme in Ref.[13], the capture resistance ability is better than the other two.
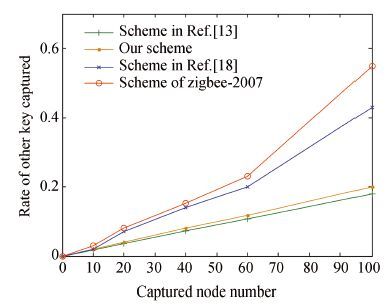
|
Figure 2 The ability to resist node capture simulation |
5.2 Key Storage Consumption Analysis
Because the memory of collector node or sink node is limited, the key storage consumption is an important indicator of key management scheme in the AMI. In our scheme, the sink node stores the public keys and identifiers, NK, LK, QC, dC, random number NC and IDC of all collector nodes; each collector node stores the public key and private key, NK, LK, random number NSi, QC and IDSi of its own. The keys stored in each node are listed in Table 4.
| Table 4 The keys stored in each node of our scheme |
In order to facilitate analysis, some assumptions are made as follows:the memory usage of a public key or a private key is p;the memory usage of an identifier or a random number is s ;the memory usage of a symmetric key is k and the number of total nodes is n. Table 5 shows the memory comparison among our scheme, scheme proposed in Ref.[13], scheme proposed in Ref.[18] and scheme of ZigBee specification 2007.
| Table 5 The memory usage comparison of four schemes |
In general, the symmetric cryptography used in ZigBee is AES, and the key length is 128 bits. The key length of ECC adopted in this paper is 160 bits, and the length of identifier or random number is 64 bits. Consequently, the detail key storage consumption of three schemes is shown in Table 6, from which we can see that the key storage in our scheme is more than that of ZigBee specification but less than that in Ref.[13] and Ref.[18], and can be implemented in smart meters. Due to using public key encryption, our scheme is nearly as secure as that in Ref.[13] but more secure than that in Ref.[18] and the security requirement in ZigBee specification.
| Table 6 The key storage of four schemes in detail |
5.3 The Time Consumption Analysis
The information transmitted in the AMI has real-time requirements;therefore, the time consumption which is composed of key computing time consumption and key distribution time consumption is another critical indicator of the key management. In this paper, we take unicast communication as an example, and the time consumption comparison between the scheme in this paper and other schemes is shown in Table 7.The CH, CMAC, CM and CE is the time consumption of Hash function, Message Authentication, ECC and symmetric cryptography respectively.
| Table 7 Time consumption of computation in each scheme |
The computation speed of ECC is slower than the speed of symmetric cryptography (such as AES).From Table 7, we can see the time consumption of computation in our scheme is less than that in Ref.[13] but more than the other two. However, the data size that the ECC deal with is very small (only the session key), so the calculation time will be tiny.Ref.[27] pointed out that the time of ECC process is 0.21 s per time in a CC2530 node. As a consequence, the time consumption of our scheme can completely satisfy the AMI information real-time requirements listed in Table 2.
As shown in Table 8, the communication interaction times in each scheme are listed. The communication interaction times in our scheme are minimized, which reduces the communication time and energy consuming.
| Table 8 The communication interaction times in each scheme |
We can also compare the key establishing time of the four schemes through simulation. Shorter time means less energy consumption. We carried on the simulation experiments of four schemes, got key generating time when the network nodes number was 10, 50, 100, 150 and 200 separately.To reduce the errors, each experiment was conducted for five times and got their mean. Experiment results are shown in Fig. 3.The minimum time needed for the key generation is the scheme with ZigBee specification, the scheme in this paper and in Ref.[18] almost cost the same time.The scheme in Ref.[13] needs the most time.The results are the same as those obtained by Tables 7 and 8.

|
Figure 3 Key generation time simulation |
6 Conclusions
In this paper, a key management scheme for ZigBee is proposed according to the system structure, message transmission patterns and security requirements in AMI. And the key establishment, key distribution and rekeying of unicast communication and multicast communication are analyzed in detail. From the analysis of security, key storage consumption and time consumption, the conclusion includes the following:1) Since the ECC is used, the security of the proposed scheme is improved;2) the storage and computation of keys can be implemented in smart meters with ZigBee communication;3) the design of the proposed scheme is closely integrated with the transmission modes of AMI and ZigBee.
| [1] |
Zhao Hongtu, Zhou Jingyang, Yu Erkeng. Advanced metering infrastructure supporting effective demand response. Power System Technology, 2010, 34(9): 13-20. ( 0) 0)
|
| [2] |
Victorian Government DPI.AMI Technology Trials Report. Department of Primary Industries, 2007.
( 0) 0)
|
| [3] |
ZigBee Alliance. ZigBee-2007 specifications. http://www. zigbee.org, 2008.
( 0) 0)
|
| [4] |
Feng Jun, NingZhigang, Yang Puqiong. Design of wireless meter reading system based on ZigBee. Electric Power Automation Equipment, 2010, 30(8): 108-111. ( 0) 0)
|
| [5] |
Li Dongdong, Cui Longlong, Lin Shunfu. Study of smart power utilization system and development of smart controller for homes. Power System Protection and Control, 2013, 41(4): 123-129. ( 0) 0)
|
| [6] |
Bilgin B E, Gungor V C. Performance evaluations of ZigBee in different smart grid environments. Computer Networks, 2012, 56(8): 2196-2205. ( 0) 0)
|
| [7] |
Huo Cheng, Shi Xiaqin, He Yigang. The research of RFID technology for smart grid. Transactions of China Electrotechnical Society, 2013, 28(S2): 383-386. ( 0) 0)
|
| [8] |
Office of the National Coordinator for Smart Grid Interoperability. NIST framework and roadmap for smart grid interoperability standards: release 1.0. USA: National Institute of Standards and Technology. 2010.
( 0) 0)
|
| [9] |
Shein R. Security measures for advanced metering infrastructure components. Proceedings of Asia-pacific Power And Energy Engineering Conference.Chengdu, 2010:1-3.
( 0) 0)
|
| [10] |
Du W, Deng J, Han Y. S, et al. A key pre-distribution scheme for sensor networks using deployment knowledge. IEEE Transactions on Dependable and Secure Computing, 2006, 3(1): 62-77. ( 0) 0)
|
| [11] |
Kong B, Chen H, Tang X, et al.Key pre-distribution schemes for large-scale wireless sensor networks using hexagon partition.Proceedings of Wireless Communications and Networking Conference (WCNC).Piscataway: IEEE,2010:1-5.
( 0) 0)
|
| [12] |
Duan M, Xu J. An efficient location-based compromise-tolerant key management scheme for sensor networks. Information Processing Letters, 2011, 111(11): 503-507. ( 0) 0)
|
| [13] |
Sahoo S K, Sahoo M N.An Elliptic-Curve-Based Hierarchical Cluster Key Management in Wireless Sensor Network.Intelligent Computing, Networking, and Informatics.Berlin:Springer,2014:397-408.
( 0) 0)
|
| [14] |
Boumerzoug H, Amar Bensaber B, Biskri I. A key management method based on an AVL tree and ECC cryptography for wireless sensor networks.Proceedings of the 7th ACM symposium on QoS and security for wireless and mobile networks.New York:ACM,2011:57-62.
( 0) 0)
|
| [15] |
Patel J S, Chavda V M. Security vulnerability and robust security requirements using key management in sensor network. Inter-national Journal of Grid & Distributed Computing, 2014, 7(3): 23-28. ( 0) 0)
|
| [16] |
Jia Tao. Research on Application of Hierarchical Access Control in Vehicle to Grid network.Beijing:North China Electric Power University, 2014. (in Chinese)
( 0) 0)
|
| [17] |
Song Jinlei.Design and Implementation of a Smart Grid Security Model for Cross-Border Interoperability Service Communication Between Substations.Xiangtan:Xiangtan University, 2014. (in Chinese)
( 0) 0)
|
| [18] |
Liu N, Chen J S, Zhu L, et al. A key management scheme for secure communications of advanced metering infrastructure in smart Grid. IEEE Transactions on Industrial Electronics, 2013, 60(10): 4746-4756. ( 0) 0)
|
| [19] |
Luan Wenpeng. Advanced metering infrastructure. Southern Power System Technology, 2009, 3(2): 6-10. ( 0) 0)
|
| [20] |
Wang Sitong, Zhou Hui, Yuan Ruiming, et al. Concept and application of smart meter. Power system Technology, 2010, 34(4): 17-23. ( 0) 0)
|
| [21] |
Kim J, Ahn S, Kim Y.Sensor network-based AMI network security.Proceedings of the Transmission and Distribution Conference and Exposition.Piscataway:IEEE PES. 2010. 1-5.
( 0) 0)
|
| [22] |
IEC TS 62351-1 Power systems management and associated information exchange-data and communications security:Part 1 communication network and system security-introduction to security issues.2007.
( 0) 0)
|
| [23] |
Lu Baohui, Ma Yonghong. Research on communication system of advanced metering infrastructure for smart grid and its data security measures. Power System Technology, 2013, 37(8): 2244-2249. ( 0) 0)
|
| [24] |
Liu Nian, Zhang Jianhua. Cyber security risks and requirement for customer interaction of smart grid. Automation of Electric Power Systems, 2011, 35(2): 79-83. ( 0) 0)
|
| [25] |
ZigBee Alliance.Smart Energy Profile 2 Application Protocol Standard.http://www.zigbee.org,2013.
( 0) 0)
|
| [26] |
Steffen F, Hans J H, Maik S.Enhancing IEC 62351 to improve security for energy automation in smart grid environments.Proceedings of the Fifth International Conference on Internet and Web Applications and Services(ICIW 2010).Barcelona:IARIA,2010:135-142.
( 0) 0)
|
| [27] |
Yu Bin, Yang Tonghao. A key distribution scheme with authentication for ZigBee. Journal of Electronics & Information Technology, 2012, 34(9): 2277-2281. ( 0) 0)
|
 2016, Vol. 23
2016, Vol. 23


