Communication networks have become an essential part of our daily lives, enabling us to connect with people and devices across the globe. These networks are used for various purposes, such as exchanging data, voice and video, and accessing online services. As the demand for communication services increases, the need for efficient and secure communication networks becomes more critical. One of the emerging areas in communication networks is Vehicular Ad-Hoc Networks (VANETs), which are designed for real-time applications through vehicles as nodes. VANETs are expected to play a significant role in improving road safety, traffic efficiency, and passenger comfort. In VANETs, reliability and safety are the primary metrics, and security is an essential aspect to ensure the safe and efficient functioning of the network[1-2].VANETs use two types of communication: one-hop and multi-hop communication. In one-hop communication, vehicles directly communicate with other vehicles in their proximity. In multi-hop communication, intermediate vehicles forward data packets to reach the destination vehicle. Road Side Units (RSUs) are also used for communication in VANETs, acting as routers to forward packets to their destination[3]. Fig. 1 shows the communication architecture of VANETs, which includes GPS, RSUs, vehicles for inter-vehicle communication, vehicle-to-RSU communication, and inter-RSU communication. Despite the potential benefits of VANETs, there are several challenges that need to be addressed, such as the lack of a centralized infrastructure, dynamic topological changes due to high vehicle speeds, and communication barriers in urban environments[4]. These challenges require the development of efficient routing protocols that can establish dynamic routes for the exchange of data in VANETs. Moreover, security is a critical aspect of VANETs that must be addressed to ensure the safe and secure functioning of the network[5]. This paper presents a review of the currently available routing techniques and the security challenges in VANETs. The paper also discusses the need for a trustworthy network architecture to address the current security challenges.

|
Fig.1 VANET communication architecture |
Even though VANET is the buzz word to autonomous transportation of inter connected vehicles, there are some issues in the characteristics of VANET that need to be addressed. Since there is no fixed infrastructure, each vehicle in VANET should establish an ad hoc architecture without any centralized AP. Another important characteristic of VANET is that it should adapt to dynamic topological changes due to the high speed of the vehicles. Buildings are the barriers to communicate among vehicles when they are entering urban environments, and the exchange of data between vehicles may not be possible. Therefore, the routing protocols should be designed in an efficient way to handle the characteristics of the VANET[6]. There are many routing protocols emerged in recent years for efficient routing of information in the network. The primary requirements of the routing protocols are that they should establish dynamic routes for the exchange of data in VANET since there are many topological changes possible in the move[7]. VANET is different from other ad hoc networks because of their dynamic characteristics in mobility due to the fast movement of vehicles and the dynamic change of topology. To cope up with these characteristics, VANET is capable of self-configuring and self-organizing nature where all the nodes can act as a router to forward the packet to other nodes. One of the primary issues in VANET is to deal with high mobility. Since the nodes in VANET are moving fast, it is very difficult to protect the nodes and their locations to make the data transfer more secure. The following are some of the unique characteristics of VANET that need to be considered before designing the routing protocols for VANET.
1) Because the nodes in VANET are frequently changing their position, many unpredictable topological changes might occur during the communication process which leads to too many connectivity issues that degrade the performance of the network.
2) The network area of VANET could be unbounded since the area of VANET can be extended without limit. It can connect two or more cities or even countries for the establishment of communication in VANET. Therefore, exchange of information in VANET is a challenging task in this unbounded network size.
3) The nodes in the VANET consume more power while transmitting the data from one node to another node. Therefore, the protocols should be designed with the consideration of this important characteristic so that exchange of information can be done with less power consumption. However, unlike MANET the power consumption is not a major challenge since the vehicles exhibit power via long life battery.
4) Because the vehicles in VANET are moving with high speed up to 150 km/h, the network achieves high mobility and for this reason, the communication link exists between vehicles might be disconnected frequently that leads to packet loss and delay. Hence, transmission power should be increased to achieve uninterrupted communication. However, increase in transmission power might affect the throughput of the network that leads to performance degradation.
5) VANETs are infrastructure less network that do not require any physical medium for communication among vehicles. When the vehicles cannot communicate directly and they are in the situation to communicate to an infrastructure, only few resources such as RSU and TAs are used in VANET. However, safety and physical protection should be considered to safeguard these resources.
The main motivation behind this work is to present the detailed study of currently available routing techniques and security challenges in VANETs. The paper also discusses the need for trustworthy network architecture in order to address the current security challenges. The other parts of the paper are divided as follows: Previous studies and existing routing schemes are discussed in Section 1. In Section 2, routing protocols and their classifications are analysed. In Section 3, the major issues in the routing protocols are discussed. Section 4 describes the research challenges in VANWT. The work is concluded in Section 5.
1 Literature SurveyAuthors in Ref.[8] proposed a centralized routing method for VANET with mobility prediction. The arrival rate of the vehicles is calculated using the non-homogeneous Poisson model. The routing table holds the global information to be utilized for the purpose of SDN controller. With the density of vehicle as the standing point, the transmission metrics increase variably using centralized routing. But, the work does not include the arrival time metric of the vehicle for accurate prediction in the network performance. Authors of Ref.[9] provided a model to examine the overall stall in a unidirectional stream. The probability that the overall latency is less than a particular threshold can be estimated using the probability distribution. The impacts of various parameters are studied to reduce latency time for gaining keen knowledge in data distribution of VANETs. But the proposed method does not fit for bi-directional VANETs. In Ref.[10], the authors proposed an Implicit Network of Trust (IWOT-V) trust model in VANET in which untrusted nodes are identified and avoided. The concept of IWOT-V is based on page ranking algorithms such as Page Rank. Although VANET lacks an explicit link structure due to its random topology and dynamic connections, social trust relationships do exist between vehicles and an implicit trust network can be derived. This paper also needs to study the random distribution of local trust values to avoid internal and external attacks. Authors of Ref.[11] discussed about the challenges in VANET. The work also proposed a novel idea for providing dynamic link where the topologies are constructed using unit disk graph model. To make the study and results more practical, a Dynamic Evolution Network (DEN) model is employed, which uses the real vehicle trajectories as input, such as node additions, deletions, and link losses. This work is not suitable for large-scale vehicle trajectory datasets in urban and rural scenarios. Authors in Ref.[12] proposed a fast and trusted transmission of sensitive data in an urban environment. The paper uses the Parking Area Assisted Spider Routing Protocol (PASRP) to handle fast message transactions. Using geographic information systems and digital maps, PASRP created a parking lot-based spider web transport model. The paper could be expanded further in generating the priority for urgent data during transmission. In Ref.[13], the authors proposed an architecture with a new optimization-based packet routing method that uses flow instantiation (FI) operations to accurately characterize link dynamics. However, research efforts have not focused on the nature of adaptive reactive protocols. Authors of Ref.[14] have presented a traffic data in real time, sharing the information using the distribution technique with road-side devices with minimal processing complexity and redundancy. But the paper does not focus on the important metrics of on load balancing and worldwide optimization in the traffic road network. In Ref.[15], the authors proposed an efficient routing method based on a flooding to improve data delivery reliability. The work does not reflect the load balance between VANET nodes and the urban transport infrastructure, as well as the presence of buildings, bridges, tunnels, etc. The research work does not include the real map scenario to evaluate the effectiveness of the method with no assumption. Authors of Ref.[16] proposed a technique to predict the false contents using a hidden Markov model. They found that their proposed model was too significant to the cut off value in different test conditions. However, there is no proper evidence that the proposed model is better than the other models and the results obtained in the work are not well established. Authors of Ref.[17] proposed a model for calculating the downlink delay in the suburban area. Significance over time and latency during node deployment plays a crucial factor in the model. The overall view of the work is to provide better services in the end point. The work does not focus on determining the urban delay calculation. The work in Ref.[18] proposed that during data transmission, when network issue occurs, it is envisaged that a temporal relay can recover the connection via store-carry-forward relay. An embedded Markov chain model is put forward to calculate the latency value using probability. However, the paper does not address the calculation of restoration delay in the downstream direction. Authors of Ref.[19] devised a model for large-scale transmission schemes with sensitive data. The paper proposed spider-web-like transmission to compare with the essential quality metrics used during transmission. The focus does not cover the task of normal data flow of the devised environment. In Ref.[20], authors proved that when the density of vehicle is high, the measure of distance between vehicle and the intersection increases naturally but the highness of message delivery decreases rapidly. It proves a major enhancement to the message dissemination. Message relaying is preferable to no relaying. But the work does not explore the significance of barriers on LOS communication performance. In Ref.[21], authors provided a verification mechanism to protect VANETs against rogue edge attackers who emit spoofing signals. During the same moving trace, the technique takes advantage over the onboard unit using the mobile's radio signal. Authors of Ref.[22] provided a Traffic Aware Data Offloading strategy for autonomous vehicular system for massive congested information centred applications. The work also analyzed TRADING using real-world data sets of traffic values in order to further assess the approach's trust and performance. Authors in Ref.[23] suggested the system which is proved to be very secure. An in-depth review of the alternatives demonstrates that the suggested approach provides superior security and usefulness. It can be extended to Internet of Vehicles systems for security measures as future development.
From the literature review, we learned that all of the work is proportional to one another. More the performance more the computational complexity and vice versa. Even though many routing schemes are available, yet there is no efficient routing scheme to find the optimal route. Most of the existing schemes depend on topological based routing scheme which is not fit for rural areas and frequent disconnection may occur. Therefore, we propose a trust-based routing scheme that will select the node based on its trust values and the secure communication can be established in terms of security, trust and privacy.
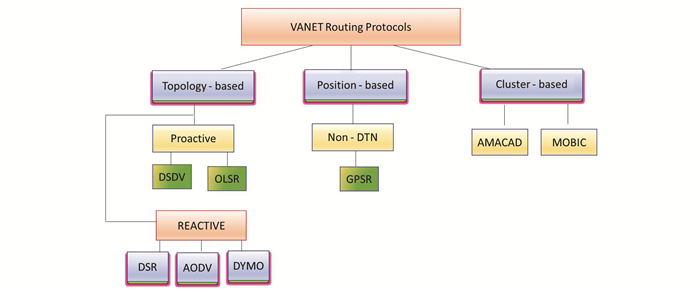
2 Routing Protocols of VANETRouting performs the transmission of packet from source node to destination node through the optimal route. The routing protocols are generally classified as topology based routing and geographical based routing. The important characteristics of these protocols are that they should be able to manage the mobility of nodes and the topological changes that occurs during the communication. Fig. 2 shows the classification of various VANET protocols.
|
Fig.2 VANET routing protocols |
2.1 Topology Based Routing
Topology-based routing protocols perform packet transmission based on the link information received from the nodes in the network. In case of multi-hop communication, intermediate nodes are selected based on the information entered in the routing table to transmit the packet to the destination. This protocol is adapted from MANET and can be further classified into proactive and reactive protocols.
Proactive protocol is a table-driven protocol where nodes are exchanged their routing table periodically in order to update the routing information. In this type, the paths for all the nodes are already built and the source node can immediately transfer the message to destination node without initiating any routing discovery process. Reactive protocol will start finding the path only upon the request received from the nodes. Here no decision is taken for selecting the best route for a node until the route request has arrived. Hence it reacts only upon request and it is also called on demand routing protocols[18]. Unlike reactive protocol, proactive will maintain the routing information for all the nodes connected in the network, and this information is updated periodically to select the best route. A combination of reactive and proactive protocol is the hybrid approach. This routing process must be secured and reliable in terms of energy consumption, computational overheads, packet loss, delay, and throughput to optimize IoT network.
2.1.1 Destination sequence distance vector routingThe Destination-Sequenced Distance-Vector (DSDV) protocol is based on traditional distance vector routing scheme where all the nodes in the network share their distance information to the neighbours. In DSDV, the routing table of each node in the network consists of the details of the destination nodes and the next hop to each of its destination to transfer the message immediately from source to destination. This routing table is dynamically updated with latest information about the next hop node and the destination node through advertisement packets. However, this protocol is suitable only for the nodes in single hop and it is not suitable for multi hop nodes.
2.1.2 OLSROptimized Link State Routing Protocol (OLSR) is based on link state information and the topology changes are updated periodically. This protocol guarantees the low latency while transferring the data. However, selecting alternate path is difficult during link failure, it requires more computational time than the other schemes.
2.1.3 DSR (Dynamic Source Routing)DSR protocol is a reactive-based protocol which will react upon the route request. The advantage of this protocol is that it will efficiently cope up with the network during the change of topology and the computational complexity is low when compared to other protocols. This protocol consists of two phases. First phase is for route discovery process and the second phase is for route maintenance. Sender will initiate route discovery process to find the destination node for message transportation. The intended recipient node will respond to the sender with the route for transferring the message. Therefore, DSR supports the establishment of ad hoc network, and each node has the capabilities of self-organization and self-configuration nature.
One advantage of DSR is that it supports the establishment of ad hoc networks where each node has self-organization and self-configuration capabilities. This means that nodes can join or leave the network without requiring any centralized control. However, the protocol suffers from a high overhead due to the route discovery process, which can result in network congestion and reduced network performance.
2.1.4 Ad Hoc On-Demand Distance Vector (AODV)This is one of the reactive protocols and reacts only when the route request is arrived. This protocol consists of 3 phases: route discovery, route establishment, and route maintenance phase. RREQ is used in route discovery process, RREP is used in route establishment and RERR is used in route maintenance[19]. It supports multi hop routing. However, it required extra bandwidth for sending the network messages. The advantage of AODV is that it can adapt to changes in network topology by dynamically discovering and maintaining routes. It also supports multi-hop routing, which allows data to be transmitted over multiple nodes to reach the destination node. However, the protocol requires extra bandwidth for sending control messages like RREQ and RREP, which can lead to increased network congestion. The protocol also requires frequent route maintenance messages to be sent to maintain the established routes, which can cause additional overhead in the network.
The advantage of AODV is that it can adapt to changes in network topology by dynamically discovering and maintaining routes. It also supports multi-hop routing, which allows data to be transmitted over multiple nodes to reach the destination node. However, the protocol requires extra bandwidth for sending control messages like RREQ and RREP, which can lead to increased network congestion. The protocol also requires frequent route maintenance messages to be sent to maintain the established routes, which can cause additional overhead in the network.
2.1.5 Dynamic MANET on-demand (DYMO)This protocol is a hybrid protocol which supports both proactive and reactive processes and is an enhanced version of AODV. Unlike AODV, it contains only 2 phases: route discovery and route maintenance. Here intermediate nodes are used to carry the RREQ packet to find the destination node and these nodes are aware of backward path. Therefore, path accumulation is simple in DYMO than AODV. This protocol is used effectively in multi hop networks.
DYMO is designed to support both unicast and multicast communication, making it suitable for applications such as mobile conference, gaming, and collaborative working. It can also handle high-mobility scenarios and can quickly adapt to topology changes in the network. In addition, DYMO is compatible with Internet Protocol version 6 (IPv6) and can be used in a range of MANET scenarios, including military and emergency response applications.
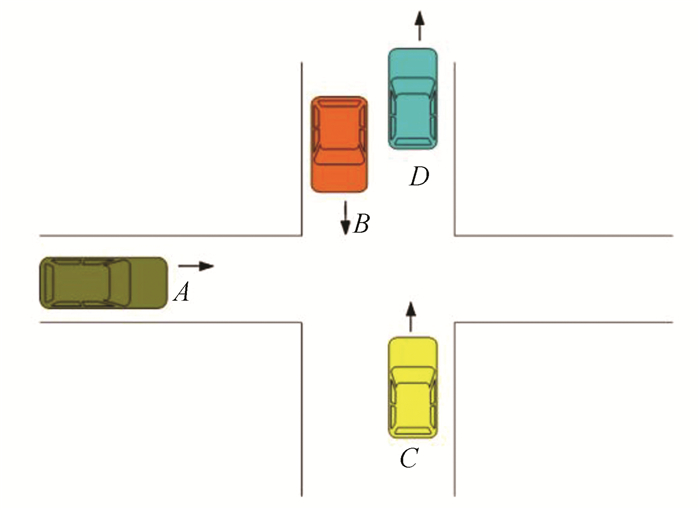
2.2 Geographical Based RoutingThis protocol is a position-based routing protocol that will use the location information to forward a message instead of a network address. Unlike topology-based protocol, pre constructed routing is not required. Every node in the network is aware of its own location and the sender can forward the message to recipient using the position information of nodes. Therefore, the complex process of route discovery and prior knowledge topology is not required. A packet can be forwarded to road intersections to reach the gateway node using the real time information of individual vehicles[20]. The packet needs to be forwarded to RSU if no neighbour nodes in the network and the frequent dynamic routing is possible. Fig. 3 shows the selection of vehicles to forward the packet based on location information of vehicles. Here, vehicle A will forward the packet to vehicle B since it is closest to A in north direction.
|
Fig.3 Packet forwarding based on the position of vehicle |
2.2.1 Non-delay tolerant network
N-DTN is based on geographical routing model that can transfer packets easily to the destination node with the knowledge of destination position. The knowledge about the position of destination node is acquired through neighbour node which is near to the destination node. Even though the message transfer process is quick, if there are no neighbour nodes near the target node, the forwarding of packets can be failed. This protocol follows the greedy technique and the main idea of this protocol is to reduce the delay for transporting the message from sender to receiver. GSR (Geographic Source Routing) is one of N-DTN which uses location-based services to identify the target node. This protocol is the combination of topological routing and position-based routing protocols[21]. The shortest route can be established by the source node using Dijkstra's shortest route algorithm. Hence, packet forwarding is done based on the position of the target and the shortest route is established between source and destination. Here centralized mechanism such as coordinator is needed to pass the packets to the destination. First, the sender will request the location information through packet broadcasting, and the receiver node will reply with location information to the sender. The disadvantage of this method is that it uses beacon frame which causes routing overhead during the transmission of packets.
2.2.2 Greedy Perimeter Stateless Routing Protocol (GPSR)GPSR is a position-based routing protocol which forwards the packet to the destination using greedy forwarding strategy based on the position of router and the target node. This decision is possible for a sender with the help of one hop router in the network. Perimeter of the area is used in the protocol through state information about the local topology when the packet cannot reach the destination and the position information is not known. Therefore, greedy forwarding and perimeter forwarding are the two important techniques used by GPSR to route the packets from source to destination[22]. It's a dynamic protocol which can effectively handle the route information even in the mobility scenario. This protocol is well scalable when the size of the network is increased.
GPSR is a stateless protocol, meaning that it does not require any global network state information to route packets. It also adapts to network changes dynamically, since it continuously updates the routing information based on the location of the nodes. However, one potential drawback of GPSR is that it may not always find the shortest path to the destination, especially in situations where the location information is not accurate or the network is highly dynamic.
2.3 Cluster Based Routing ProtocolThe vehicles in a nearby region form a cluster and each vehicle is considered as a node in a network. All the nodes are communicated directly in case of intra cluster communication while all the nodes are communicated via coordinator node called cluster head in case of inter cluster communication. If any node sends data to other node inside the network, then it can be established via direct link. If a node wants to send data to nodes in other clusters, then it can be established via cluster head[23]. As far as VANET is concerned, establishment of route is difficult because of the mobility characteristics of each node in the network. Adaptable Mobility-Aware Clustering Algorithm based on destination (AMACAD) and MOBIC are used in inter cluster communication. AMACAD is used as an effective routing mechanism that prevents re-clustering of nodes by transmitting the data from source to destination without the complex overhead. MOBIC is used to compute the mobility of a node based on signal strength of the mobile node and the location information can be gathered with the help of neighbour nodes.
In the Cluster-Based Routing Protocol, vehicles in a nearby region form a cluster, and each vehicle is considered a node in the network. The nodes communicate directly in case of intra-cluster communication, while communication between clusters is done through a coordinator node called the cluster head. This method of communication helps to reduce the number of messages transmitted, which in turn reduces the network overhead and improves network efficiency.
When a node sends data to another node inside the same cluster, the communication takes place via a direct link. However, when a node wants to send data to nodes in other clusters, the communication takes place through the cluster head. This is because the establishment of a route in VANETs is difficult due to the mobility characteristics of each node in the network.
To facilitate inter-cluster communication, the Cluster-Based Routing Protocol uses routing mechanisms like Adaptable Mobility-Aware Clustering Algorithm based on destination (AMACAD) and MOBIC. AMACAD is an effective routing mechanism that prevents re-clustering of nodes by transmitting data from the source to the destination without complex overhead. MOBIC, on the other hand, computes the mobility of a node based on the signal strength of the mobile node, and location information can be gathered with the help of neighbour nodes.
Overall, the Cluster-Based Routing Protocol is an efficient and scalable solution for VANETs, which can handle the dynamic nature of the vehicular environment. It is particularly useful in dense urban areas where there are large number of vehicles and a high demand for efficient communication between them.
3 Major Issues in Routing ProtocolsThere are several factors such as high mobility, density of the network, environmental condition and many more that affect the performance of the VANET. In topology-based routing, proactive protocol supports the fast transmission of data from one vehicle to another vehicle since the routes are readily available prior to data transmission. But the routing tables need to be updated frequently so that transmission can be done smoothly without delay[24]. However, maintenance of updated routing information in VANET requires more control packets which each node in the network should broadcast to update its current status. This process of sending updated connectivity information on regular basis is tedious and it leads to additional overhead. Reactive protocol will allocate the route only upon request and they will not maintain any routing information in advance. Even though it minimizes the overhead of maintaining update information in proactive scheme, the route discovery process makes the data transmission complex even if one node faces link failure. The drawback of topology-based routing scheme is that it cannot cope up with the frequent topological changes due to the high velocity of vehicles. Therefore, this kind of routing is not suitable for highly dynamic environment.
Location based routing in VANET does not maintain any route prior to data transmission rather it depends on the neighbour nodes to forward the packets using position related information. This kind of routing can be effective in dynamic environment since the routing of packets are done through location information whereas topology-based routing depends on current topological information that needs to be updated on regular basis otherwise frequent link failure will occur. Even though, location-based routing serves well, message delivery might be delayed if the optimal neighbour node is not chosen properly.
The selection of best neighbour node is the challenging task in VANET and it is its own responsivity to carry the packets from sender to destination[25]. Each vehicle in a network should be aware of its neighbours and a beacon frame is broadcasted over the network periodically by a node to inform its current position related information[26-27]. This frame can be frequently broadcasted by each node in the network to confirm its updated position that may flood the network.
On the other hand, cluster-based routing plays an important role in VANET for reducing the energy consumption of nodes in the network. To coordinate the vehicles, a cluster head should be there so that the nodes in the network can communicate with each other without interruption. However, the selection of cluster head is based on the stability of a node in the network.
Therefore, a cluster head should be selected based on the node's stability rate. But this could not be suitable of dynamic environment since the vehicles are moving fast to one or more location areas. Therefore, it is necessary to evaluate the performance of the routing protocols. The performance should be analysed in terms of packet drop and throughput since the VANET is highly mobile in nature. Summary of the previous schemes are given in Table 1.
| Table 1 Summary of existing schemes |
4 Simulation Tools
There are many simulation tools used in various research works for the communication between RSU and vehicles in VANET. The simulation for the transmission power of the VANET can be done through SWAN (Scalable Wireless Ad hoc Network Simulator) which will be run over JIST. This simulation is arrived especially for VANET since the existing schemes cannot cope up with current research requirements.
The benefit of SWAN is that it achieves high throughput by eliminating memory copy and context switch, it saves memory by sharing the single copy with multiple nodes, and supports existing applications such as web servers to run over the simulation without interruption.OMNET ++ is the other important discrete event simulator for VANET to deal with the components of the network such as routing. The components are required for wireless technologies and routing protocols are provided by INET while RSU and vehicle related components are provided by VEINS (Vehicles In Network Simulation). To support link layer, INET provides protocols such as OSPF(Open Source Shortest Path First) and BGP (Background Gateway Protocol). To provide communication in simulation environment, VEINS uses OMNET++ for interaction with INET. Simulation parameters used in the evaluations are routing protocols, bandwidth, radio type, radio band etc. SUMO is another simulator for the analysis of VANET which comprises many tools for the evaluation of traffic simulation to create road networks and route computation with emitted cost of the vehicles. Many VANET based algorithms were evaluated by SUMO for checking the effect of parking of autonomous vehicles and their traffic performance with enhanced throughput and packet drop. Some of the simulation parameters used in SUMO are vehicle class, traffic density, simulation time, departure time, car following model etc. Intelligent driver model can react to any environment changes such as changing the lane of the vehicles or going in wrong route. The pros and cons of the simulation tools are given in Table 2.
| Table 2 Analysis of VANET simulation tools |
5 Research Challenges in VANET
There are many challenges that needs to be addressed to enhance the performance of the VANET despite many research have been emerged for improving the performance of VANET, still there are many challenges to be addressed in various areas of VANET to enhance the performance of the network. Basically, the challenges of VANET can be viewed as network challenges and security challenges. High mobility is one of the network challenges since the nodes in VANET are highly movable in their own direction. The important difficulty in the network is that it could not perform congestion control because of the frequent topological changes. All the nodes are communicated through EM signals and the data in the network could be easily corrupted or blocked by the attackers since EM signals are open in the environment. Another important challenge is the distribution of private keys for secret communication among the nodes in the network, and for this reason authentication of each node in this dynamic environment is difficult. Also, integrity of data is questionable since the correct sequence of data may not be possible for the recipient node. Environmental barriers are also possible since EM waves are used in the VANET for communication. Among all the challenges, the life critical application such as road safety in VANET should be protected with confidentiality and integrity. Therefore, our proposal is to establish a trust-based routing scheme that will isolate the malicious traffic from the network by selecting only the trusted nodes with less computational overhead.
6 ConclusionsBased on the investigation and analysis of the nomenclature of routing path in the VANET environment, this study has identified several non-performing tasks and provided various information related to the VANET environment. The results of this study can be useful for researchers who wish to implement their proposed work in both real-time and simulation scenarios. Additionally, this paper has described the nature of VANET, its characteristics, and highlighted the security challenges that need to be addressed to protect sensitive data.To evaluate the performance of these routing protocols, custom-built monitoring tools were used to record the performance metrics of the routing protocols. The work demonstrates that AODV outperforms DSR and DSDV in terms of throughput and delay, while DSR consumes the least energy. Additionally, we observed that the performance of the routing protocols varied with the density of vehicles and mobility patterns of the nodes. Our study highlights the importance of conducting real-world experiments to evaluate the performance of routing protocols in VANETs, as they provide more realistic and accurate results than simulation-based studies.
Moving forward, our findings can aid in the selection and design of efficient and secure routing protocols for VANETs. However, more research is needed to address the security, trust, and privacy issues associated with current routing mechanisms. Future research can focus on developing trusted-based routing mechanisms for VANET that consider these issues. Additionally, more experiments can be conducted to evaluate the performance of routing protocols in various VANET environments with different traffic densities and mobility patterns. This can lead to the development of more robust and efficient routing protocols for VANET, which can significantly enhance the performance and security of VANET networks.
| [1] |
Tang Y, Cheng N, Wu W, et al. Delay-minimization routing for heterogeneous VANETs with machine learning based mobility prediction. IEEE Transactions on Vehicular Technology, 2019, 68(4): 3967-3979. DOI:10.1109/TVT.2019.2899627 (  0) 0) |
| [2] |
Seliem H, Shahidi R, Ahmed M H, et al. On the end-to-end delay in a one-way VANET. IEEE Transactions on Vehicular Technology, 2019, 68(9): 8336-8346. DOI:10.1109/TVT.2019.2916936 (  0) 0) |
| [3] |
Xiao Y, Liu Y. Bayes Trust and Vehicle Rank: Constructing an implicit web of trust in VANET. IEEE Transactions on Vehicular Technology, 2019, 68(3): 2850-2864. DOI:10.1109/TVT.2019.2894056 (  0) 0) |
| [4] |
Qu X, Liu E, Wang R, et al. Complex network analysis of VANET topology with realistic vehicular traces. IEEE Transactions on Vehicular Technology, 2020, 69(4): 4426-4438. DOI:10.1109/TVT.2020.2976937 (  0) 0) |
| [5] |
Liu H, Qiu T, Zhou X, et al. Parking-area-assisted spider-web routing protocol for emergency data in urban VANET. IEEE Transactions on Vehicular Technology, 2020, 69(1): 971-982. DOI:10.1109/TVT.2019.2954159 (  0) 0) |
| [6] |
Sudheera K L K, Ma M, Chong P H J. Link stability based optimized routing framework for software defined vehicular networks. IEEE Transactions on Vehicular Technology, 2019, 68(3): 2934-2945. DOI:10.1109/TVT.2019.2895274 (  0) 0) |
| [7] |
Guo C, Li D, Zhang G, et al. Real-time path planning in urban area via VANET-assisted traffic information sharing. IEEE Transactions on Vehicular Technology, 2018, 67(7): 5635-5649. DOI:10.1109/TVT.2018.2806979 (  0) 0) |
| [8] |
Oubbati O S, Chaib N, Lakas A, et al. UAV-Assisted supporting services connectivity in urban VANETs. IEEE Transactions on Vehicular Technology, 2019, 68(4): 3944-3951. DOI:10.1109/TVT.2019.2898477 (  0) 0) |
| [9] |
Yeung C Y, Hui L C K, Chim T W, et al. Anonymous counting problem in trust level warning system for VANET. IEEE Transactions on Vehicular Technology, 2019, 68(1): 34-48. DOI:10.1109/TVT.2018.2884899 (  0) 0) |
| [10] |
Al Zamil M G, Samarah S, Bennis M, et al. False-alarm detection in the fog-based internet of connected vehicles. IEEE Transactions on Vehicular Technology, 2019, 68(7): 7035-7044. DOI:10.1109/TVT.2019.2917288 (  0) 0) |
| [11] |
Wu Y, Zheng J. Modeling and analysis of the local delay in an MEC-based VANET for a suburban area. IEEE Internet of Things Journal, 2022, 9(9): 7065-7079. DOI:10.1109/JIOT.2021.3116195 (  0) 0) |
| [12] |
Huang J-J, Tseng Y T. The steady-state distribution of rehealing delay in an intermittently connected highway VANET. IEEE Transactions on Vehicular Technology, 2018, 67(10): 10010-10021. DOI:10.1109/TVT.2018.2865500 (  0) 0) |
| [13] |
Qiu T, Wang X, Chen C, et al. TMED: A spider-web-like transmission mechanism for emergency data in vehicular Ad Hoc networks. IEEE Transactions on Vehicular Technology, 2018, 67(9): 8682-8694. DOI:10.1109/TVT.2018.2841348 (  0) 0) |
| [14] |
Noor-A-Rahim M, Nawaz Ali G G Md, Guan Y L, et al. Broadcast performance analysis and improvements of the LTE-V2V autonomous mode at road intersection. IEEE Transactions on Vehicular Technology, 2019, 68(10): 9359-9369. DOI:10.1109/TVT.2019.2936799 (  0) 0) |
| [15] |
Lu X, Xiao L, Xu T, et al. Reinforcement learning based PHY authentication for VANETs. IEEE Transactions on Vehicular Technology, 2020, 69(3): 3068-3079. DOI:10.1109/TVT.2020.2967026 (  0) 0) |
| [16] |
Darwish T S J, Bakar K A, Kaiwartya O, et al. TRADING: Traffic aware data offloading for big data enabled intelligent transportation system. IEEE Transactions on Vehicular Technology, 2020, 69(7): 6869-6879. DOI:10.1109/TVT.2020.2991372 (  0) 0) |
| [17] |
Sutrala K, Bagga P, Das A K, et al. On the design of conditional privacy preserving batch verification-based authentication scheme for internet of vehicles deployment. IEEE Transactions on Vehicular Technology, 2020, 69(5): 5535-5548. DOI:10.1109/TVT.2020.2981934 (  0) 0) |
| [18] |
Baee M A R, Simpson L, Foo E, et al. Broadcast authentication in latency-critical applications: on the efficiency of IEEE 1609.2. IEEE Transactions on Vehicular Technology, 2019, 68(12): 11577-11587. DOI:10.1109/TVT.2019.2945339 (  0) 0) |
| [19] |
Cui J, Wang Y, Zhang J, et al. Full session key agreement scheme based on chaotic map in vehicular Ad Hoc networks. IEEE Transactions on Vehicular Technology, 2020, 69(8): 8914-8924. DOI:10.1109/TVT.2020.2997694 (  0) 0) |
| [20] |
Ajmal S, Rasheed A, Qayyum A, et al. Classification of VANET MAC, routing and approaches a detailed survey. Journal of Universal Computer Science, 2014, 20(4): 462-487. (  0) 0) |
| [21] |
Rasheed A, Zia H, Hashmi F, et al. Fleet & convoy management using VANET. Journal of Computer Networks, 2013, 1(1): 1-9. (  0) 0) |
| [22] |
Feroz Khan A B, Hanna Lalitha R, Kalpana Devi S, et al. A multi-attribute based trusted routing for embedded devices in MANET-IoT. Microprocessors and Microsystems, 2022, 89: 104446. DOI:10.1016/j.micpro.2022.104446 (  0) 0) |
| [23] |
Sak H, Senior A W, Beaufays F. Long short-term memory recurrent neural network architectures for large scale acoustic modeling. INTERSPEECH 2014, 15th Annual Conference of the International Speech Communication Association, Singapore, 2014.
(  0) 0) |
| [24] |
Kumar R, Dave M. A comparative study of various routing protocols in VANET. International Journal of Computer Science Issues (IJCSI), 2011, 8(4): No. 4. DOI: 10.48550/arXiv.1108.2094
(  0) 0) |
| [25] |
Paul B, Islam M J. Survey over VANET routing protocols for vehicle to vehicle communication. IOSR Journal of Computer Engineering (IOSRJCE), 2012, 7: 1-9. (  0) 0) |
| [26] |
Secinti G, Canberk B, Duong T Q, et al. Software defined architecture for VANET: A testbed implementation with wireless access management. IEEE Communications Magazine, 2017, 55(7): 135-141. DOI:10.1109/MCOM.2017.1601186 (  0) 0) |
| [27] |
Feroz Khan A B F, Hussain M M, Kalpana Devi S, et al. DDoS attack modeling and resistance using trust-based protocol for the security of internet of things. Journal of Engineering Research, 2023, 11(2): 100058. DOI:10.1016/j.jer.2023.100058 (  0) 0) |
 2023, Vol. 30
2023, Vol. 30


