2. Department of Information Technology, Mohamed Sathak AJ College of Engineering,Siruseri, Chennai 603103, India;
3. Department of Information Technology, Panimalar Engineering College, Chennai 600123, India;
4. Department of Information Technology, C. Abdul Hakeem College of Engineering and Technology, Melvisharam 632509, India
The Internet of Things (IoT) has ushered in a new era of connectivity, where a vast array of devices, from household appliances to industrial sensors, can communicate and exchange data autonomously. This paradigm shift in networking has brought about unparalleled convenience and efficiency in various sectors. However, the rapid proliferation of IoT devices has also exposed them to significant security vulnerabilities and performance challenges. The necessary background, motivations, and objectives behind the proposal of a trust-based routing mechanism for IoT networks are provided in this section.
1) Background
IoT networks are characterized by their decentralized nature, allowing devices to join or exit the network dynamically, often without human intervention. Traditional network security mechanisms, which rely on centralized control and fixed infrastructure, are ill-suited to the dynamic and distributed nature of IoT networks. These networks are vulnerable to various security threats, including data breaches, device impersonation, and denial-of-service attacks. Moreover, ensuring reliable data transmission is crucial in IoT applications, where real-time data from sensors or actuators may be critical for decision-making. One approach to addressing these IoT network challenges is multipath routing. Multipath routing, such as the Ad hoc On-demand Multipath Distance Vector (AOMDV) protocol, enables devices to establish multiple data transmission paths simultaneously. This not only enhances reliability by mitigating the impact of path failures but also balances the network load, ensuring efficient resource utilization.
2) Motivations
The motivations behind the integration of a trust-based routing mechanism in IoT networks are multifold:
A. Security enhancement:trust-based routing introduces an additional layer of security by evaluating the trustworthiness of nodes within the network. By considering the historical behavior and interactions of devices, the network can make informed decisions to avoid compromised or malicious nodes. This helps safeguard sensitive IoT data and mitigate the risks associated with unauthorized access or data tampering.
B. Optimized resource utilization:Multipath routing, like AOMDV, is known for its ability to improve network performance by utilizing multiple transmission paths. When coupled with a trust model, the routing decisions can be optimized not only for reliability but also for trustworthiness. This leads to more efficient data transmission and resource allocation.
C. Adaptability to dynamic environments:IoT networks are highly dynamic, with devices entering and leaving the network frequently. Trust-based routing mechanisms can adapt to these changes by continuously evaluating and updating the trustworthiness of nodes. This adaptability is crucial in maintaining network integrity and performance in evolving IoT scenarios.
3) Objectives
The primary objectives of this research are:
A. Integration of AOMDV with a trust model:Investigate the feasibility and benefits of integrating the AOMDV multipath routing protocol with a trust model tailored to IoT networks. This integration aims to leverage both the reliability of multipath routing and the security enhancements provided by trust evaluations.
B. Evaluation of trust-based routing performance:Conduct comprehensive simulations to assess the impact of trust-based routing on IoT network performance. Specifically, measure improvements in security, routing efficiency, and overall network reliability achieved through this approach.
In summary, this research addresses the pressing need for improved security and performance in IoT networks by proposing a trust-based routing mechanism. By integrating AOMDV with a trust model and evaluating its performance, we aim to provide a holistic solution that can mitigate security risks and optimize data transmission paths in the ever-expanding world of IoT.
1 Related workThe Internet of Things (IoT) has witnessed exponential growth in recent years, connecting an ever-expanding array of devices, from smart homes to industrial sensors. These IoT networks are characterized by their decentralized and dynamic nature, allowing devices to join or leave the network autonomously. While IoT offers unparalleled convenience and efficiency, it also presents significant challenges, particularly in terms of security and network performance.
Traditional network security measures, often designed for centralized and fixed infrastructure, struggle to adapt to the unique characteristics of IoT networks. The dynamic nature of IoT devices and the wireless communication channels they use make these networks susceptible to various security threats, including unauthorized access, data breaches, and malicious attacks. Additionally, ensuring reliable data transmission is paramount, especially in critical IoT applications such as healthcare and industrial automation.
To address these challenges, researchers have explored various approaches to enhance IoT network security and performance. One promising avenue involves the integration of trust-based routing mechanisms, which evaluate the trustworthiness of network nodes and use this information to make routing decisions. This integration can potentially mitigate security risks, optimize data transmission paths, and improve the overall efficiency of IoT networks. In this context, we review a selection of studies and research efforts that contribute to the understanding and advancement of trust-based routing, multipath routing, and security in IoT networks.
Authors of Ref.[1] comprehensively covered trust-based routing mechanisms in IoT networks. It discusses various trust models and their applications, providing an excellent foundation for understanding the role of trust in enhancing IoT network security and performance. The study highlighted the importance of trust as a means to evaluate the reliability of nodes in IoT networks, which can influence routing decisions and mitigate security risks.
Authors of Ref.[2] introduced a trust-aware multipath routing scheme designed to improve both security and performance in IoT networks. By incorporating trust evaluations into routing decisions, the scheme aims to route data through trustworthy paths, thus enhancing network reliability. This approach acknowledges the dynamic and often unreliable nature of IoT networks and leverages trust to adaptively route data.
In Ref.[3], the authors discussed security challenges in IoT networks and explored potential solutions.Trust-based approaches are among the strategies considered to address IoT security issues. The study provides valuable insights into the broader context of security in IoT, highlighting the need for innovative solutions like trust-based routing.
Ref.[4] focused on evaluating different multipath routing protocols in IoT scenarios. While not solely trust-based, it provides insights into the performance of multipath routing in terms of reliability and load balancing. Multipath routing is a crucial component in enhancing IoT network performance, and understanding its performance characteristics is essential.
Authors of Ref.[5] concentrated on IoT in vehicular networks and proposed a trust-based data forwarding mechanism to improve communication reliability. It acknowledges the importance of trust in vehicular IoT, where safety-critical data is often transmitted. This work underscores the role of trust in ensuring data integrity and security in specific IoT applications.
Authors in Ref.[6] explored a wide range of security and trust issues in IoT applications and discussed potential solutions. It provides a comprehensive overview of security challenges across various IoT domains, making it valuable for understanding the broader context of trust-based routing in IoT networks.
Ref.[7] investigated trust-based routing mechanisms specifically tailored to wireless sensor networks within IoT environments. Wireless sensor networks are a fundamental component of IoT, and trust-based routing can enhance their reliability and security. This work focused on the unique characteristics of sensor nodes and their impact on trust-based routing.
Authors of Ref.[8] proposed a trust-based routing protocol to ensure the confidentiality and integrity of patient data. Trust is a critical factor in healthcare IoT, where data privacy and security are paramount. This work emphasizes the significance of trust in sensitive IoT applications.
Ref.[9] explored the use of multipath routing to balance load and enhance reliability in IoT networks. While not primarily trust-based, it contributes to the understanding of multipath routing's impact on performance. Load balancing is a crucial aspect of IoT network optimization.
Authors of Ref.[10] introduced a trust-based routing protocol optimized for energy efficiency in IoT applications. It acknowledges the resource constraints of IoT devices and aims to route data efficiently while considering trustworthiness. Energy efficiency is a critical concern in many IoT deployments, and this work addresses this challenge.
Ref. [11] not only focused on routing, but also provided insights into security and trust issues in IoT healthcare systems. It emphasized the significance of security and trust in healthcare IoT, shedding light on the broader context of trust-based routing in this domain.
The proposed work builds upon the insights gained from the surveyed literature and addresses critical issues by integrating a trust model with the Ad hoc On-demand Multipath Distance Vector (AOMDV) routing protocol in IoT networks. It overcomes the limitation of solely surveying trust-based routing mechanisms[1] by implementing and evaluating a practical application of trust-based routing in IoT scenarios. Additionally, it effectively addresses the challenge of enhancing both security and performance in IoT networks [2] by dynamically adapting routing decisions based on trustworthiness, thus offering a comprehensive solution. Moreover, it contributes to the broader context of IoT security and trust[3] by introducing a concrete implementation of trust-based routing, demonstrating how it can mitigate security risks and optimize data transmission paths in the IoT landscape. This work bridges the gap between theoretical trust-based concepts and their real-world application in IoT networks.
2 MethodologyIn the context of Mobile Ad hoc Networks (MANETs), blackhole attacks represent a significant security concern. These attacks occur when malicious nodes falsely advertise fresh destination routes to attract data packets and subsequently drop them, leading to severe disruptions in data communication [12-19]. To mitigate these attacks, this proposed work introduces a trust-based routing mechanism specifically tailored for IoT networks. The trust model incorporated in this proposal encompasses several crucial properties:
Context dependency: Trust relationships are context-dependent, meaning they have significance only within specific contexts. In IoT networks, context-aware trust evaluations are essential due to the diverse nature of applications and communication scenarios.
Uncertainty function: Trust assesses the likelihood of an entity performing a specific action, reflecting the uncertainty inherent in trust evaluations. In IoT, where nodes' behavior can vary widely, accounting for uncertainty is crucial.
Predictive capability: Trust evaluates the probability of an entity carrying out a particular action. In IoT, predicting the trustworthiness of nodes is essential for making informed routing decisions.
Quantitative values: Trust can be represented using continuous or discrete numeric values, enabling quantitative assessment. In IoT, numeric trust values facilitate objective decision-making.
Asymmetry: Trust relationships can be asymmetric, meaning that if Node A trusts Node B, it does not necessarily imply that Node B trusts Node A. Asymmetry accounts for variations in trust perceptions among IoT devices.
Transitivity: Trust is typically transitive, where if Node A trusts Node B and Node B trusts Node C, then Node A should trust Node C. However, real-world trust may not always adhere to perfect transitivity.
Personalization: Trust is subjective and personalized. Individuals or devices may evaluate the trustworthiness of the same entity differently based on their unique experiences and interactions within the network.
2.1 Ad Hoc On-demand Multipath Distance Vector (AOMDV)To implement trust-based routing in IoT networks, the Ad hoc On-demand Multipath Distance Vector (AOMDV) routing protocol serves as the foundation. AOMDV is an extension of the AODV routing protocol, specifically designed to enable multiple paths in route discovery. It ensures the disjointedness of links in multiple paths, preserving loop freedom by employing sequence numbers to nodes[20].
A distinguishing feature of AOMDV is the periodic use of HELLO messages to detect link failures. Routing entries in AOMDV maintain a list of subsequent hops along with their hop counts for tracking multiple paths. Duplicate route promotions signify alternate paths to the destination if the hop count for a path is less than the promoted value, ensuring loop freedom. This allows AOMDV to find node-disjoint or link-disjoint routes, offering flexibility in routing decisions[21-24].
2.2 Proposed Trust ModelThe proposed trust model in this work plays a pivotal role in enhancing security and routing efficiency in IoT networks. Trust evaluation, computation, and application are essential components of this model. Trust is derived from the packet forwarding ratio of nodes, reflecting their reliability in the network. A linear aggregate technique is employed to estimate the trust of individual nodes based on trust factors, while the trust of a path is evaluated using the least value method.
Direct trust, a component of the trust model, relies on firsthand information obtained from neighbors. It is calculated using the history of direct interactions among nodes, simplifying trust computation. Trust evaluation occurs during the routing process, marking the sender's trust in the service of a forwarding node. This evaluation is crucial in the presence of security threats like gray hole and black hole attacks, heavy traffic, and poor wireless communication, as it assesses the quality of packet forwarding[25-28].
The trust model incorporates Control packet Forwarding Ratio (CFR) and Data packet Forwarding Ratio (DFR) as trust factors. These trust factors are assigned weights, and direct trust between nodes is represented as Tjk, where CFR and DFR are observed by node j for forwarding node k. Trust values from these factors are weighted and combined to determine the total trust level for a node.
In route discovery, the trust model detects route request flooding attacks, monitoring packet generation from the source node. The source node's trust value is initially set to one. The trust value is evaluated based on route discovery, with the network being informed by an Intrusion Detection System (IDS). The IDS checks the trust value for all neighboring nodes, and if the source node's trust value falls below a threshold, it is dropped, thwarting potential attacks[25].
This proposed trust model, integrated with AOMDV, enhances security and reliability in IoT networks by enabling context-aware, predictive, and personalized trust evaluations, thus mitigating the impact of blackhole attacks and ensuring the trustworthiness of routing decisions.
Algorithm 1: Trust Evaluation Algorithm.
This algorithm outlines the process of evaluating the trustworthiness of individual nodes within the IoT network based on their behavior, interactions, and packet forwarding performance.
Input:
·Packet forwarding history (correct forwarding and total requests)
·Trust factors (Control packet Forwarding Ratio (CFR) and Data packet Forwarding Ratio (DFR))
·Weighting parameters (w1 and w2 for CFR and DFR, respectively)
Output:
Trust score for each node.
Procedure:
1)Initialize trust scores for all nodes to 1.
2)For each node j in the network:
·Calculate CFRjk(ti) and DFRjk(ti) based on packet forwarding history.
·Compute direct trust Tjk using weighted aggregation of CFRjk(ti) and DFRjk(ti).
3)Repeat steps 2) for all neighboring nodes.
4)Update the trust scores for each node based on the calculated direct trust values.
Algorithm 2: Trust-based Routing with AOMDV.
This algorithm combines the trust model with the AOMDV routing protocol to make routing decisions that consider both trustworthiness and routing metrics.
Input:
Trust scores for all nodes.
AOMDV routing information (routing tables, sequence numbers, hop counts).
Output:
Trust-aware routing decisions.
Procedure:
1)Initialize routing tables, sequence numbers, and hop counts in AOMDV.
2)Periodically send HELLO messages to detect link failures and update routing tables.
3)When a source node initiates route discovery:
·Calculate trust values for neighboring nodes using the trust model.
·Send Route Request (RREQ) packets to neighbors with trust values above a threshold.
4)Intermediate nodes receiving RREQs:
·Evaluate the trustworthiness of the source node based on its trust score.
·Forward RREQs only if the source node's trust is above a threshold.
·Maintain a list of next hops and their associated hop counts for potential multiple paths.
5)Destination node:
·Respond to RREQs with Route Reply (RREP) packets.
·Include trust-aware path information in RREPs.
6)Source node:
· Receive RREPs with trust-aware path information.
·Select routes based on trust values and routing metrics (e.g., hop count).
7)Route maintenance:
·Continuously monitor trust scores and routing metrics.
· Re-evaluate routes and update them dynamically based on trust and network conditions.
The trust evaluation algorithm assesses the trustworthiness of individual nodes within the IoT network based on their behavior and packet forwarding performance. It begins by initializing trust scores for all nodes. Then, for each node in the network, it calculates trust factors such as the Control packet Forwarding Ratio (CFR) and Data packet Forwarding Ratio (DFR) using packet forwarding history. Using weighted aggregation of CFR and DFR with assigned parameters, it computes a direct trust value (Tjk) for each node. This process is repeated for all neighboring nodes, and the trust scores are updated based on the calculated direct trust values. The result is a trust score assigned to each node, reflecting their reliability in the network. This trust evaluation is a fundamental component of the proposed trust-based routing mechanism, influencing routing decisions that consider both trustworthiness and traditional routing metrics, ultimately enhancing security and efficiency in IoT networks.
3 Results and DiscussionTo evaluate the effectiveness of the proposed trust-based routing mechanism in the context of IoT networks, we conducted a series of simulation experiments using a customized Wireless Sensor Network (WSN) model implemented in MATLAB. In these experiments, we deployed a total of 200 nodes randomly within a two-dimensional area measuring 1000×1000 units. Each node was initially endowed with an energy capacity of 2 J. Data packets used in the experiments had a fixed size of 30 bits.
We designed two distinct scenarios to assess the mechanism's performance under varying conditions. In the first scenario, 5% of the nodes within the network were designated as malicious, simulating a realistic environment where a limited number of nodes may act maliciously. In the second scenario, the proportion of malicious nodes was increased to 10%, representing a more hostile network environment.
The following performance metrics were recorded during the experiments:
Packet Delivery Ratio (PDR):This metric measures the proportion of data packets successfully delivered to their intended destinations, reflecting the reliability of data transmission.
End-to-End Delay: End-to-end delay quantifies the transmission time of a data packet from the source node to the destination node. It provides insights into data transfer efficiency.
Number of hops to destination: The number of hops represents the count of intermediate nodes that a data packet passes through before reaching its final destination. Fewer hops generally indicate more efficient routing.
Percentage of malicious nodes detected: This metric assesses the mechanism's ability to detect and mitigate malicious nodes within the network.
The experimental results are presented in Tables 1 to 4, providing a comprehensive overview of the mechanism's performance in mitigating security threats, optimizing data transmission, and maintaining network reliability under different scenarios. These results offer valuable insights into the practical applicability of the proposed trust-based routing mechanism in real-world IoT deployments.
| Table 1 Packet delivery ratio |
| Table 2 Average End to End Delay in second |
| Table 3 Average number of hops to destination |
| Table 4 Percentage of malicious node detected |
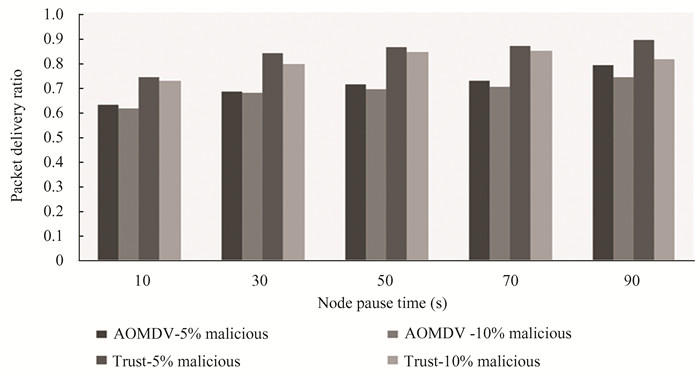
From Fig. 1, it can be observed that the proposed trust model with 5% malicious nodes improved the packet delivery ratio by 20.02% more than AOMDV protocol with 5% malicious nodes with node pause time of 30 s. And proposed trust model with 10% malicious nodes improved the packet delivery ratio by 19.96% than AOMDV protocol with 10% malicious nodes with node pause time of 50 s.
|
Fig.1 Analysis of packet delivery ratio |
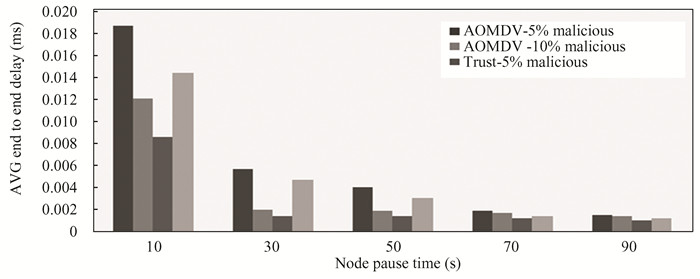
From Fig. 2, it can be observed that the proposed trust model with 5% malicious nodes decreased the end to end delay by 40% than AOMDV protocol with 5% malicious nodes with node pause time of 30 s. And proposed trust model with 10% malicious nodes decreased the end to end delay by 19.96% than AOMDV protocol with 10% malicious nodes with node pause time of 50 s.
|
Fig.2 Average delay analysis |
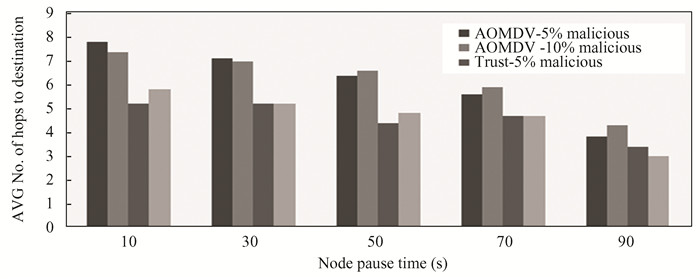
From Fig. 3, it can be observed that the proposed trust model with 5% malicious nodes achieved number of hops to destination by 40% than AOMDV protocol with 5% malicious, and the proposed trust model with 10% malicious nodes achieved number of hops to destination by 24.24% than AOMDV protocol with 10% malicious nodes with node pause time of 10 s.
|
Fig.3 Number of hops to destination in average |
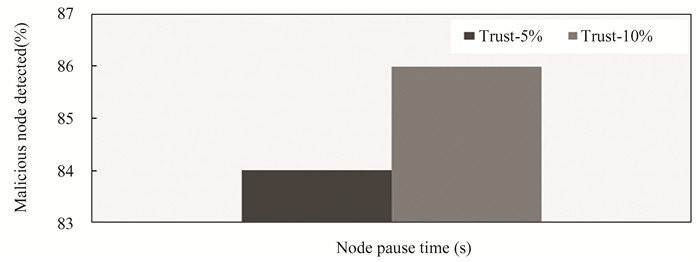
The simulation experiments yielded valuable insights into the proposed trust-based routing mechanism's ability to detect and mitigate malicious nodes within the IoT network. Notably, in Fig. 4, we observed a noteworthy improvement in the detection of malicious nodes when 10% of the nodes in the network were designated as malicious, as compared to the scenario with 5% malicious nodes. Specifically, the proposed trust model with 10% malicious nodes improved the percentage of malicious nodes detected by 2.35% compared to the trust model with 5% malicious nodes. This finding underscores the mechanism's enhanced resilience in hostile network environments, where a higher proportion of nodes may exhibit malicious behavior. The ability to identify and isolate such nodes contributes significantly to network security and data integrity, making the proposed trust-based routing mechanism a robust choice for IoT applications.
|
Fig.4 Detection rate |
In the realm of securing Internet of Things (IoT) networks, several works and research efforts have contributed to enhancing security, reliability, and efficiency. In this comparative analysis, we evaluate the proposed trust-based Trust Model against two conventional methods: Energy-Efficient Multipath Based Trust Routing (EMBTR) and Conventional Energy-Multipath Trust (CEMT) protocols. Each of these works aims to address the security challenges posed by IoT networks, but they employ different strategies and mechanisms to achieve these objectives.
1) Average delay
Average delay in the context of this research refers to the time taken for data to traverse from its source to its destination. It is quantified by assessing the time difference between the packet's transmission and its reception, encompassing factors such as processing and queuing delays as data traverses from one node to another. The computation of average transmission delay is represented with ‘n’ denoting the count of nodes in the network.
Fig. 5 provides a graphical depiction of the average transmission delay, comparing the proposed trust-based Trust Model (TTSM) scheme with conventional methods, namely Energy-Efficient Multipath Based Trust Routing (EMBTR) and Conventional Energy-Multipath Trust (CEMT) protocols. The results clearly demonstrate that the proposed TTSM scheme achieves a significantly lower data transmission delay when compared to EMBTR and CEMT protocols.
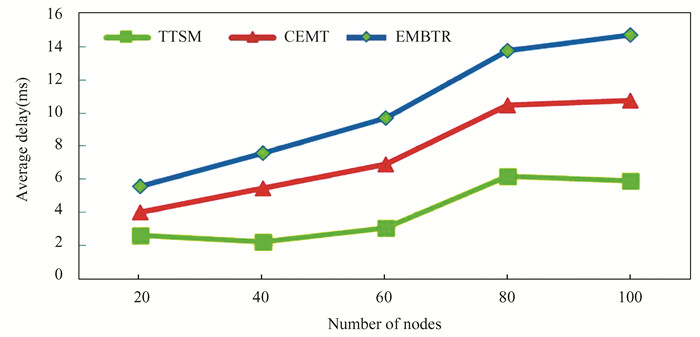
|
Fig.5 Average delay |
2) Delay relative to time intervals of various attacks
In this context, we explore the average delay associated with specific types of attacks, including Black Hole Attacks (BHA), Gray Hole Attacks (GHA), and Wormhole Attacks (WHA), concerning different time intervals. Fig. 6 illustrates the average delay for these various attacks across different time intervals. Among these attack models, the GHA model emerges as particularly detrimental to network performance. Consequently, identifying and mitigating malicious nodes is imperative. By ensuring the anonymity of nodes, secure data transmission is facilitated through trusted and reliable routes. Detecting and isolating malicious nodes significantly enhances network reliability and security. The proposed TTSM model demonstrates its reliability by reducing transmission delay in the face of these attacks.
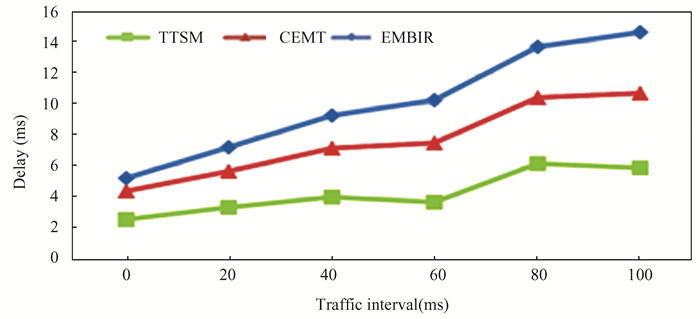
|
Fig.6 Delay relative to various attacks |
3) Energy consumption
Energy consumption, in this context, quantifies the energy expended by nodes for data processing and transmission. It involves periodic measurement of energy levels in nodes, considering both initial and remaining energy levels. Fig. 7 presents a graphical representation of energy consumption, comparing the proposed TTSM model with existing EMBTR and CEMT techniques.
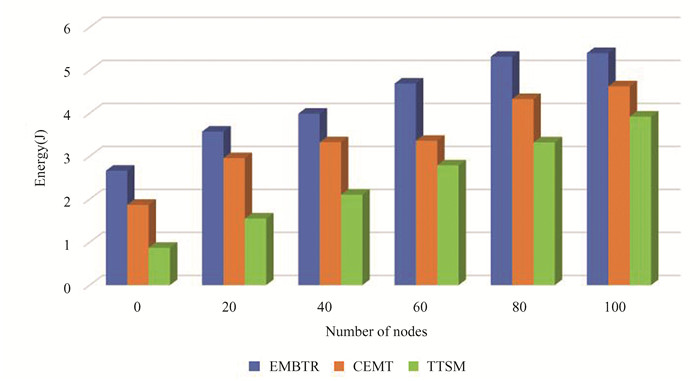
|
Fig.7 Energy consumption |
The results highlight that the TTSM model consumes substantially less energy per transmission cycle, even with varying node counts, when contrasted with EMBTR and CEMT protocols. This observation underscores the suitability of the selected routes in TTSM as resource-efficient and highly reliable.
4) False node detection ratio
The False Node Detection Ratio (FNDR) measures the detection ratio between normal nodes and malicious nodes based on their behavior. Normal nodes forward packets without alterations or losses, while malicious nodes eavesdrop on packets and forward false information, often with delays. Fig. 8 presents a graphical representation of FNDR, comparing the proposed TTSM scheme with existing EMBTR and CEMT schemes.
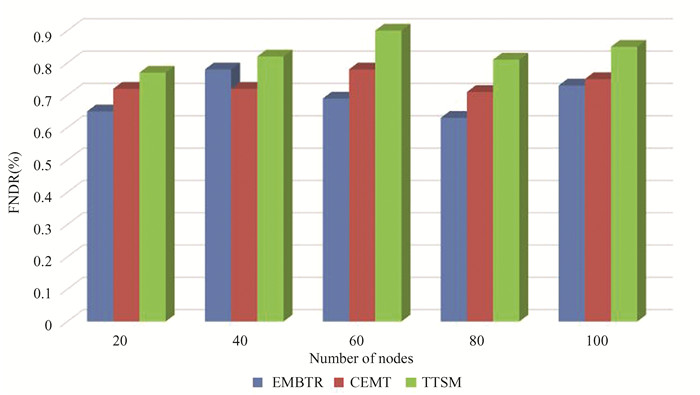
|
Fig.8 False node detection rate |
The average FNDR for the proposed TTSM model is 0.83, indicating a high capability to detect malignant nodes in the network. In contrast, both conventional schemes, EMBTR and CEMT, exhibit FNDR values of 0.652 and 0.750, respectively. These results establish that the FNDR for the TTSM model outperforms the conventional schemes, affirming its effectiveness in identifying and mitigating malicious nodes.
4 ConclusionsIn the rapidly evolving landscape of the Internet of Things (IoT), ensuring the security and reliability of data transmission is of paramount importance. This research has presented a comprehensive investigation into the integration of a trust-based routing mechanism with the Ad hoc On-demand Multipath Distance Vector (AOMDV) routing protocol to address the unique challenges posed by IoT networks. Through a series of simulation experiments conducted in a customized Wireless Sensor Network (WSN) model, the efficacy of the proposed mechanism has been demonstrated and analyzed. The results of these experiments have shown that the proposed trust-based routing mechanism offers a promising solution to enhance the security and efficiency of IoT networks. Notably, the mechanism exhibited improved performance in scenarios where a higher percentage of malicious nodes was present, indicating its robustness in hostile network environments. It successfully detected and mitigated malicious nodes, contributing to network security and data integrity. Furthermore, the integration of multipath routing capabilities with trust-based routing has shown promise in optimizing data transmission, reducing end-to-end delay, and enhancing the overall reliability of IoT networks. The adaptability of the mechanism to context-dependent trust evaluations and personalized trust perceptions among devices further enhances its applicability in diverse IoT scenarios. In conclusion, this research has provided valuable insights into the potential benefits of trust-based routing in IoT networks. By combining security measures, multipath routing, and adaptive trust evaluations, the proposed mechanism offers a holistic approach to address the evolving challenges of IoT communication. As IoT continues to grow and evolve, trust-based routing mechanisms represent a vital component in ensuring the security and reliability of data transmission in these dynamic and interconnected networks. Future research in this area may explore additional trust models, scalability considerations, and practical implementations to further advance the state of IoT security and efficiency.
| [1] |
AlRubaiei M, Shaker H, Sharef B, et al. Current vulnerabilities, challenges and attacks on routing protocols for mobile ad hoc network: a review. Swarm Intelligence for Resource Management in Internet of Things, 2020, 109-129. DOI:10.1016/B978-0-12-818287-1.00012-7 (  0) 0) |
| [2] |
Khan A B, Hannah Lalitha R, Kalpana Devi K, et al. A multi-attribute based trusted routing for embedded devices in MANET-IoT. Microprocessors and Microsystems, 2022, 89: 104446. DOI:10.1016/j.micpro.2022.104446 (  0) 0) |
| [3] |
Valaboju Y. Routing and vulnerabilities in MANETS. International Journal of Multidisciplinary Research In Science, Engineering and Technology (IJMRSET), 2018, 1(2): 247-252. (  0) 0) |
| [4] |
Alo R U, Stanly N I, Onwe N F. Mobile Ad Hoc Network (MANET): applications, benefits and performance issues in a global positioning system. International Research Journal of Engineering and Technology, 2018, 5(11): 983-987. (  0) 0) |
| [5] |
Yi J, Adnane A, David S, et al. Multipath optimized link state routing for mobile ad hoc networks. Ad Hoc Networks, 2011, 9(1): 28-47. DOI:10.1016/j.adhoc.2010.04.007 (  0) 0) |
| [6] |
Kalidoss T, Rajasekaran L, Kanagasabai K, et al. QoS aware trust based routing algorithm for wireless sensor networks. Wireless Personal Communications, 2020, 110(4): 1637-1658. DOI:10.1007/s11277-019-06788-y (  0) 0) |
| [7] |
Hassnawi L A, Ahmad R B, Yahya A, et al. Performance analysis of various routing protocols for motorway surveillance system cameras' network. International Journal of Computer Science Issues, 2012, 9(2): 7-21. (  0) 0) |
| [8] |
Mesleh A. Black hole attack evaluation for AODV and AOMDV routing protocols. International Journal of Electronic Security and Digital Forensics, 2018, 10(3): 207-227. DOI:10.1504/IJESDF.2018.092994 (  0) 0) |
| [9] |
Feroz Khan A B, Karthick B, Matheena M. Securing the internet of things: challenges, strategies, and future directions. Research and Applications Towards Mathematics and Computer Science, 2023, 6: 119-141. DOI:10.9734/bpi/ratmcs/v6/11074F (  0) 0) |
| [10] |
Azimi I, Anzanpour A, Rahmani A M, et al. HiCH: hierarchical fog-assisted computing architecture for healthcare IoT. ACM Transactions on Embedded Computing Systems, 2017, 16(5s): Article No.174.DOI: 10.1145/3126501.
(  0) 0) |
| [11] |
Azimi I, Takalo-Mattila J, Anzanpour A, et al. Empowering healthcare IoT systems with hierarchical edge-based deep learning. In Proceedings of the 2018 IEEE/ACM International Conference on Connected Health: Applications, Systems and Engineering Technologies. Piscataway: IEEE, 2018. 63-68.DOI: 10.1145/3278576.3278597.
(  0) 0) |
| [12] |
Kollu V N, Janarthanan V, Karupusamy Muthulakshmi, et al. Cloud-based smart contract analysis in FinTech Using IoT-integrated federated learning in intrusion detection. Data, 2023, 8(5): 83. DOI:10.3390/data8050083 (  0) 0) |
| [13] |
Bierzynski K, Escobar A, Eberl M. Cloud, fog and edge: cooperation for the future? In 2017 Second International Conference on Fog and Mobile Edge Computing. Piscataway: IEEE, 2017. 62-67.DOI: 10.1109/FMEC.2017.7946409.
(  0) 0) |
| [14] |
Masip-Bruin X, Marin-Tordera E, Alonso A, et al. Fog-to-cloud computing (F2C): the key technology enabler for dependable e-health services deployment. In 2016 Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net).Vilanova i la Geltru, 2016. 1-5.DOI: 10.1109/MedHocNet.2016.7528425.
(  0) 0) |
| [15] |
Liu C, Cao Y, Luo Y, et al. A new deep learning-based food recognition system for dietary assessment on an edge computing service infrastructure. IEEE Transactions on Services Computing, 2017, 11(2): 249-261. DOI:10.1109/TSC.2017.2662008 (  0) 0) |
| [16] |
Chen C M, Agrawal H, Cochinwala M, et al. Stream query processing for healthcare bio-sensor applications. Proceedings of the 20th International Conference on Data Engineering.Piscataway: IEEE, 2004.751.DOI: 10.1109/ICDE.2004.1320048.
(  0) 0) |
| [17] |
Abdellatif A A, Mohamed A, Chiasserini C F, et al. Edge computing for smart health: context-aware approaches, opportunities, and challenges. IEEE Networks, 2019, 33(3): 196-203. DOI:10.1109/MNET.2019.1800083 (  0) 0) |
| [18] |
Alwan O S, Rao K P. Dedicated real-time monitoring system for health care using ZigBee. Healthcare Technology Letters, 2017, 4(4): 142-144. DOI:10.1049/htl.2017.0030 (  0) 0) |
| [19] |
Akmandor A O, Jha N K. Smart health care: an edge-side computing perspective. IEEE Consumer Electronics Magazine, 2017, 7(1): 29-37. DOI:10.1109/MCE.2017.2746096 (  0) 0) |
| [20] |
AAlthaf Ali A, Hussain M M, Subramaneswara Rao A, et al. Enhancing security in the internet of things: a trust-based protocol for resilient communication. SN Computer Science, 2024, 5: Article number: 4. DOI: 10.1007/s42979-023-02329-4.
(  0) 0) |
| [21] |
Karunkuzhali D, Meenakshi B, Lingam K. OQR-SC: an optimal QoS aware routing technique for smart cities using IoT enabled wireless sensor networks. Wireless Personal Communications, 2022, 125(4): 3575-3602. DOI:10.1007/s11277-022-09725-8.3602 (  0) 0) |
| [22] |
Abdel-Basset M, Manogaran G, Gamal A, et al. A novel intelligent medical decision support model based on soft computing and IoT. IEEE Internet of Things Journal, 2019, 7(5): 4160-4170. DOI:10.1109/JIOT.2019.2931647 (  0) 0) |
| [23] |
Ferrag M A, Maglaras L A, Janicke H, et al. Authentication protocols for internet of things: a comprehensive survey. Security Communication Networks, 2017, 2017: Article ID 6562953.DOI: 10.1155/2017/6562953.
(  0) 0) |
| [24] |
Madhuri N S, Shailaja K, Saha D, et al. IOT integrated smart grid management system for effective energy management. Measurement: Sensors, 2022, 24: 100488. DOI:10.1016/j.measen.2022.100488 (  0) 0) |
| [25] |
Feroz Khan A B, Anandharaj G. The embedded framework for securing the internet of things. Journal of Engineering Research: Computer Engineering, 2021, 9(2): Article 9823. DOI: 10.36909/jer.v9i2.9823.
(  0) 0) |
| [26] |
Korzhuk V, Groznykh A, Menshikov A, et al. Identification of attacks against wireless sensor networks based on behaviour analysis. J Wirel Mobile Netw Ubiquit Comput Dependable Appl (JoWUA), 2019, 10(2): 1-21. DOI:10.22667/JOWUA.2019.06.30.001 (  0) 0) |
| [27] |
Feroz A B F, Devi K. An enhanced AES-GCM based security protocol for securing the IoT communication. Scientific and Technical Journal of Information Technologies, Mechanics and Optics, 2023, 23(4): 711-719. DOI:10.17586/2226-1494-2023-23-4-711-719 (  0) 0) |
| [28] |
Khan A B F, Hussain M M, Devi S K, et al. DDoS attack modeling and resistance using trust based protocol for the security of Internet of Things. Journal of Engineering Research, 2023, 11(2): 100058. DOI:10.1016/j.jer.2023.100058 (  0) 0) |
 2024, Vol. 31
2024, Vol. 31


