2. Information Technology, Anil Neerukonda Institute of Technology & Science(Autonomous), Sangivalasa 531162, Bheemunipatnam, India
Network attacks pose a significant threat to the security and integrity of networked systems in today's interconnected world. Detecting and mitigating these attacks is a difficult multidomain task requiring multiple steps, including packet capture, pre-processing, feature analysis, classification, and post-processing. When applied to real-time data samples, existing models addressing these tasks are frequently complicated or inefficient. This paper introduces a novel approach for designing an efficient forensic layer for mitigating hybrid attacks by integrating deep learning pattern analysis, multidomain feature extraction, and evolutionary optimization techniques in order to address these limitations[1-3]. This work is necessary due to the increasing prevalence and sophistication of hybrid attacks, which exploit networked system vulnerabilities using multiple attack vectors. These attacks pose significant difficulties for conventional security measures, necessitating the development of innovative techniques capable of detecting and mitigating them effectively.
The application of multidomain feature extraction is one of the major contributions of this paper. The proposed model captures a comprehensive representation of network traffic patterns by incorporating a variety of feature extraction techniques, including Fourier transform, Z transform, Laplace transform, Discrete Cosine Transform (DCT), 1D Haar wavelet, Gabor transform, and convolutional operations. This multidomain strategy permits a comprehensive data analysis, enabling the detection of subtle anomalies indicative of hybrid attacks. In addition, the use of multidomain features improves the model's robustness and adaptability, allowing it to withstand a variety of attack scenarios. The dragonfly optimizer is utilized to improve the effectiveness and efficiency of feature selection. By identifying the most informative and discriminative features, this evolutionary optimization algorithm effectively reduces the dimensionality of the feature space. Using the dragonfly optimizer, the proposed model improves accuracy and computational efficiency, enabling detection and mitigation to be performed in real-time environments via Bayesian Inference (BI) process[4-6]. The proposed forensic layer is centred on the integration of VGGNet and GoogLeNet via binary cascaded neural networks. These models of deep convolutional neural networks have demonstrated outstanding performance in a variety of computer vision tasks and are adept at extracting high-level abstract features from complex data.
Using the power of these models, the proposed system is able to analyze network traffic patterns and identify potential anomalies indicative of hybrid attacks. The binary cascaded architecture augments the model's capabilities by facilitating efficient feature fusion and decision-making procedures. There are numerous benefits to utilizing multidomain features, the dragonfly optimizer, and CNN models. The incorporation of multidomain features enables a thorough and robust representation of network traffic, thereby facilitating the detection of complex attack patterns that span multiple domains. By selecting the most informative features, the dragonfly optimizer reduces the dimensionality of the feature space, enabling faster processing and improved accuracy. The integration of VGGNet and GoogLeNet models via Binary Cascaded Neural Networks improves the model's ability to recognize complex patterns, enabling accurate and timely hybrid attack detection. The proposed model is applicable in a number of use cases. First, it can be used to enhance the capabilities of intrusion detection and prevention systems in enterprise networks. By providing a forensic layer, the model assists network administrators in determining the origin of attacks, assessing the extent of damage, and identifying potential vulnerabilities. This data permits proactive measures to be taken to protect networked systems. In addition, the model can be applied to networks of critical infrastructure, such as power grids and transportation systems, to detect and mitigate hybrid attacks that, if left unchecked, could have severe consequences.
This paper concludes with a novel method for designing an effective forensic layer for mitigating hybrid attacks. The proposed model enhances the capabilities of conventional intrusion detection and prevention systems by integrating deep learning pattern analysis, multidomain feature extraction, and evolutionary optimization techniques. The use of multidomain features, the dragonfly optimizer, and the integration of VGGNet and GoogLeNet models via binary cascaded neural networks result in enhanced accuracy, computational efficiency, and the ability to detect complex attack patterns. The proposed model has multiple use cases, enabling proactive defense against hybrid attacks and bolstering the security of networked systems. The rest of the paper is organized as follows. Section 1 presents review of existing models. In Section 2, design of an efficient forensic layer for mitigating hybrid attacks via deep learning pattern analysis is proposed. In Section 3, result analysis and comparison is given. In Section 4, conclusions and future work are provided.
1 Review of Existing ModelsTraditional security measures face significant challenges in defending against hybrid attacks, which involve the combination of multiple attack vectors. Researchers have developed numerous models and techniques to address this issue and improve the security of networked systems over the years. This literature review examines some of the existing hybrid attack mitigation models and identifies their strengths and weaknesses. Intrusion detection systems are widely used for detecting and mitigating network attacks. On the basis of predefined rules or machine learning algorithms, they analyze network traffic and identify anomalous behavior. Due to their reliance on predefined signatures or limited feature analysis, traditional IDS models frequently struggle to effectively detect hybrid attacks[7-9].
Machine learning techniques have been used to improve the capabilities of intrusion detection systems. For attack detection, models such as Support Vector Machines (SVM), Random Forests, and Naive Bayes classifiers have been utilized. While these models produce promising results, they frequently focus on specific attack types and may lack the ability to detect hybrid attacks that are complex and constantly evolving process.
Deep Learning Techniques: In recent years, deep learning has received considerable attention for its ability to extract complex patterns and characteristics from network traffic data. To detect network attacks, Convolutional Neural Networks (CNNs), Recurrent Neural Networks (RNNs), and Long Short-Term Memory (LSTM) networks have been utilized. Deep learning models provide the benefit of automatic feature extraction, but their performance is highly dependent on the availability of large, labelled datasets [9-11]. Ensemble learning combines multiple models to boost the overall performance of detection. To combine the outputs of multiple classifiers, techniques such as bagging, boosting, and stacking have been used. Ensemble models improve the detection system's robustness and generalizability, but may incur increased computational complexity and training overheads[10-12].
Some researchers have proposed hybrid models that combine various techniques to capitalize on their respective strengths. A hybrid model may, for instance, combine rule-based methods with machine learning or deep learning algorithms. These models are intended to identify both known attack signatures and novel attack patterns. Developing effective feature representations and striking a balance between accuracy and computational efficiency continue to be obstacles for hybrid models.
Algorithms for evolutionary optimization have been used to enhance the performance of hybrid attack detection models. For feature selection, model optimization, and parameter tuning, techniques including genetic algorithms, particle swarm optimization, and ant colony optimization have been utilized. Evolutionary optimization can effectively reduce feature dimensionality, improve detection system accuracy and efficiency levels via use of Sequential Change Point Detection (SCPD) process[13-15]. Existing models have made significant contributions to hybrid attack mitigation, but there are still a number of unexplored areas. These include the development of more effective feature extraction techniques, the investigation of adaptive and self-learning models capable of detecting emerging attack patterns, and the consideration of real-time processing needs for effective attack mitigations[16-17].
The literature review concludes by emphasizing that, although traditional IDS systems and machine learning approaches provide valuable insights, they may have limitations in detecting complex hybrid attacks. Deep learning techniques and hybrid models show promise for enhancing detection precision, but obstacles such as dataset accessibility[18-20], and computational complexity persist. Moreover, evolutionary optimization techniques enable feature selection and model optimizations via Graph Neural Networks (GNNs)[21]. Future research should concentrate on developing more robust and efficient models capable of detecting and mitigating hybrid attacks in real-time, as network threats continue to evolve for different scenarios.
2 Proposed Design of Efficient Forensic Layer for Mitigating Hybrid Attacks via Deep Learning Pattern AnalysisBased on the review of existing models used for analysis of network attacks and forensics, it can be observed that most of these models are not comprehensive in terms of feature representation & analysis. This limits their capability to identify network attacks, and trace back any anomalous events. To overcome these issues, this work proposes use of an efficient & novel feature representation method that combines Fourier transform, Z transform, Laplace transform, DCT, 1D Haar wavelet, Gabor transform and convolutional operations. As shown in Fig. 1, the proposed method fuses these features, and processes them via Dragonfly Optimization (DFO) model, which assists in selection of highly variant feature sets, that can be used to identify high-density class-level features. These features are classified into different attack classes using a fusion of VGGNet and GoogLeNet via binary cascaded neural networks.
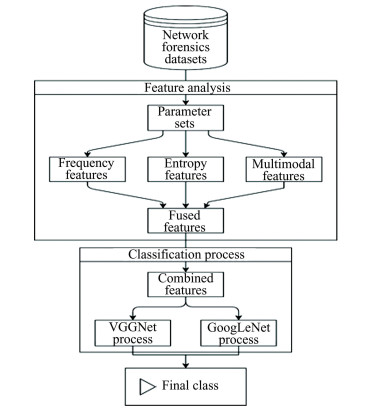
|
Fig.1 Design of the proposed model for forensic analysis |
The Fourier transform is a widely used technique for feature representation that converts a signal from the time domain to the frequency domain, revealing the spectral characteristics of the signals via Eq. (1):
| $ \begin{align*} F_{\text {req }}= & \sum\limits_{j=1}^{N_{\mathrm{f}}} F(j) \cdot\left[\cos \left(\frac{2 \pi i j}{N_{\mathrm{f}}}\right)-\sqrt{-1} ·\right. \\ & \left.\sin \left(\frac{2 \pi i j}{N_{\mathrm{f}}}\right)\right] \end{align*} $ | (1) |
where, Nf represents total number of extracted features, F represents the collected features from the network, which includes the following:
1) IP addresses: Extraction of source and destination IP addresses can aid in identifying communication endpoints and reveal potentially malicious activity. It can also help identify the origin of an attack.
2) Port numbers identify the specific network service or application in use. Analyzing port numbers can provide insight into the nature of network activities and aid in identifying potential vulnerabilities or abnormal behavior.
3) Protocol information: Extracting protocol information, such as TCP (Transmission Control Protocol) or UDP (User Datagram Protocol), can aid in the comprehension of network communication patterns and protocols.
4) Packet headers: By analyzing packet headers, valuable information about packet sequencing, packet size, fragmentation, and other parameters can be obtained. This data can be utilized to identify anomalies and potential attacks.
5) Monitoring and analyzing the traffic volume and patterns can assist in identifying abnormal spikes or dips in network activity. Unusual traffic patterns may indicate the presence of unauthorized activities or a network attack.
6) Payload content: By extracting and analyzing the payload content of network packets, one can gain insight into the transmitted datasets & samples. This analysis can reveal patterns, signatures, or anomalies that may indicate malicious activity or unauthorized disclosure of sensitive information sets.
7) Timing and timestamps: Examining the timing and timestamps of network packets can assist with establishing timelines, detecting unusual delays or response times, and correlating events across network devices or systems.
8) Network flow information: Extracting flow-level information, such as the duration of flows, number of packets per flow, and byte counts, can assist in identifying potential threats and understanding the overall network behavior.
9) Network topology: Extraction of information regarding the network's physical and logical structure can aid in the identification of potential points of vulnerability and forensic investigations.
10) Domain Name System (DNS) information extraction can provide insight into domain resolutions, hostnames, and possible malicious domain connections.
11) Extraction of session-level information, such as session start and end times, session duration, and session IDs, can assist in analyzing the flow of network communication and identifying anomalous or suspicious session behavior.
12) Network protocols: Identifying the specific network protocols used in the captured traffic, such as HTTP, FTP, SMTP, or DNS, can provide insight into the applications or services being used and assist in detecting malicious activities.
13) Analyzing the time intervals between packets within a network flow can help identify patterns, abnormal delays, and timing-based attacks.
14) Traffic patterns: Extracting traffic patterns, such as periodic, bursty, or irregular patterns, can help identify network anomalies and potential attacks, such as DoS or DDoS attacks.
15) Quality of Service (QoS) parameters: Quality of Service (QoS) parameters, such as packet loss rate, delay, or jitter, can be extracted to assess the performance and reliability of network connections and detect anomalies that may indicate network attacks or degraded performance.
16) Extraction of geo-location data from IP addresses can provide insights into the geographic origin or destination of network traffic, aiding in the identification of potential threat actors or attack sources.
17) Network delay: Analyzing network latency, such as round-trip times (RTT) or delay variations, can aid in the detection of anomalies or potential network disruptions that may indicate attacks or compromised network segments.
18) User-agent specification: Extraction of user-agent data from network packets can provide information about the software, operating systems, or devices utilized by network clients, thereby facilitating the identification of particular types of traffic or potentially malicious activities.
19) DNS request details: Analyzing DNS query data, such as query types, domain resolutions, and DNS response codes, can help identify suspicious or potentially malicious domain activities, such as DNS tunneling and domain hijacking.
20) Payload hashes: Calculating and storing cryptographic hashes of payload data can assist in identifying known malicious files or detecting changes to payload content, thereby facilitating the identification of malware or data exfiltration attempts.
Similar to fourier transform, DCT is commonly employed for feature representation, particularly in forensic applications. It transforms a signal or image into a set of cosine basis functions, emphasizing different frequency components to capture important features via Eq.(2):
| $ \begin{align*} \mathrm{DCT}= & \frac{1}{\sqrt{2 N_{\mathrm{f}}}} \cdot \sum\limits_{j=1}^{N_{\mathrm{f}}} F(j) \cdot \\ & \cos \left[\frac{\sqrt{-1} \cdot(2 i+1) \pi}{2 N_{\mathrm{f}}}\right] \end{align*} $ | (2) |
Similarly, the 1D Haar wavelet is a simple and efficient technique for feature representation process. It decomposes a signal into wavelet coefficients, capturing both high-frequency (H) details and low-frequency (L) trends, providing a compact representation of the signals via Eqs. (3) and (4) as follows:
| $L=\frac{F(i)+F(i+1)}{2} $ | (3) |
| $ H=\frac{F(i)-F(i+1)}{2} $ | (4) |
The Gabor Transform (GT) combines time and frequency analysis, providing a feature representation that captures both temporal and spectral characteristics of the collected network parameter sets. It is especially useful in estimation of long-ranged patterns, and is estimated by using the following equation:
| $ \begin{equation*} \mathrm{GT}=e^{\frac{-x^{\prime 2}+\partial^{2} y^{\prime 2}}{2 \rho^{2}}} \cdot \cos \left(2 \frac{\pi}{\lambda} \cdot F(x)^{\prime}\right) \end{equation*} $ | (5) |
where, x, y represent index and value of the parameter sets, while
Convolutional operations, commonly used in CNNs, enable effective feature representation by convolving filters or kernels over input datasets & patterns. This operation captures local patterns and spatial relationships, allowing the network to learn hierarchical representations of features in a data-driven manner for different scenarios. These features are extracted via Eq.(6):
| $ \begin{equation*} \operatorname{Conv}=\sum\limits_{a=-\frac{m}{2}}^{\frac{m}{2}} \operatorname{Arr}(i-a) \cdot \operatorname{LReLU}\left(\frac{m+2 a}{2}\right) \end{equation*} $ | (6) |
where, m, a represent the sizes of different windows and strides, while LReLU represents a non-linear kernel that uses leaky rectilinear units for activation of features. This activation is done via Eq.(7):
| $ \left\{\begin{array}{l} \operatorname{LReLU}(x)=\operatorname{la} \times x, x<0 \\ \operatorname{LReLU}(x)=x, \quad \text { else } \end{array}\right. $ | (7) |
where, la is an activation constant, used to convert all features into positive values, thus assisting in better classification performance levels.
The Z transform is used to analyze discrete-time patters from the collected network traffic, and is calculated via Eq.(8):
| $ \begin{equation*} X(z)=\sum x(n) \times z^{-n} \end{equation*} $ | (8) |
where, X(z) represents the Z-transform of the discrete-time signal x(n), and n represents the discrete-time index sets.
Similarly, the Laplace transform is used to analyze continuous-time signals and traffic patterns via Eq.(9):
| $ \begin{equation*} X(s)=\int\left[x(t) \times \mathrm{e}^{-s t}\right] \mathrm{d} t \end{equation*} $ | (9) |
where, X(s) represents the Laplace transform of the continuous-time signal x(t), and s represents the complex variable sets. All these features are fused to form a Forensic Feature Vector (FFV), which is given to a Dragonfly Optimizer (DFO) for maximization of variance levels. This optimizer works as per the following operations,
1) A set of ND dragonflies is generated via selection of stochastic features. This selection is done via Eq.(10):
| $ \begin{equation*} N=\operatorname{STOCH}(\mathrm{LD} \cdot N(\mathrm{FFV}), N(\mathrm{FFV})) \end{equation*} $ | (10) |
where, LD represents learning rate of the DFO process, while N represents the number of features extracted for this dragonfly via stochastic (STOCH) operations.
2) Using these features, fitness of the dragonflies (fd) is estimated via Eq.(11):
| $ \mathrm{fd}=\sqrt{\sum\limits_{i=1}^{N} \frac{\left(x_{i}-\bar{\bar{x}}\right)^{2}}{N}} $ | (11) |
| $\bar{\bar{x}}=\sum\limits_{i=1}^{N} \frac{x(i)}{N_{\mathrm{f}}} $ | (12) |
where x represents the selected features.
3) A set of ND such dragonflies is generated, and then their fitness threshold(fth) is estimated via Eq.(13):
| $\begin{equation*} \mathrm{fth}=\frac{1}{\mathrm{ND}} \sum\limits_{i=1}^{\mathrm{ND}} \mathrm{fd}(i) \times \mathrm{LD} \end{equation*} $ | (13) |
4) Dragonflies with fd>fth are directly passed to the next iteration, while other dragonflies are modified via Eq.(14):
| $ \begin{align*} f(\text { New })= & f(\text { Current })+s_{1} \cdot(\mathrm{fd}(\text { Current })- \\ & \operatorname{Max}(\mathrm{fd}))+s_{2} \cdot(\mathrm{fd}(\text { Current })- \\ & \operatorname{best}(\mathrm{fd})) \end{align*} $ | (14) |
where, f(New) and f(Current) represent new and current features, while Max (fd) represents maximum level of fitness across all dragonflies, while best(fd) represents best fitness of the current set of dragonflies, s1 and s2 are two stochastic number sets.
5) This process is repeated for NI iterations, and different configurations are generated for ND dragonflies.Once all iterations are completed, then dragonflies with maximum fitness are selected, and their features are used for the classification process. These features are given to a fusion VGGNet and GoogLeNet models by means of binary cascaded neural networks. This is an efficient & novel method for improving the analysis of network traffic patterns and more effectively identifying anomalies. This fusion technique makes use of the advantages of both models' strengths to get around each one's flaws and produce a more reliable and potent network security systems.
Deep architecture and outstanding performance in data classification tasks are two things that set VGGNet apart from other classifiers. The model can learn intricate patterns and feature hierarchies thanks to its many layers of tiny convolutional filters. VGGNet is well suited for the extraction of meaningful features from network traffic data due to its ability to capture detailed spatial information sets.
The idea of inception modules and parallel convolutional operations, on the other hand, was first introduced by Google's LeNet, also known as inception process. Through parallel convolutional operations, this architecture uses multiple layers with various filter sizes to incorporate both local and global features. This makes it possible for Google neural network to efficiently capture various feature representations at various scales. Fig. 2 shows the design of both VGGNet model and GoogLeNet.
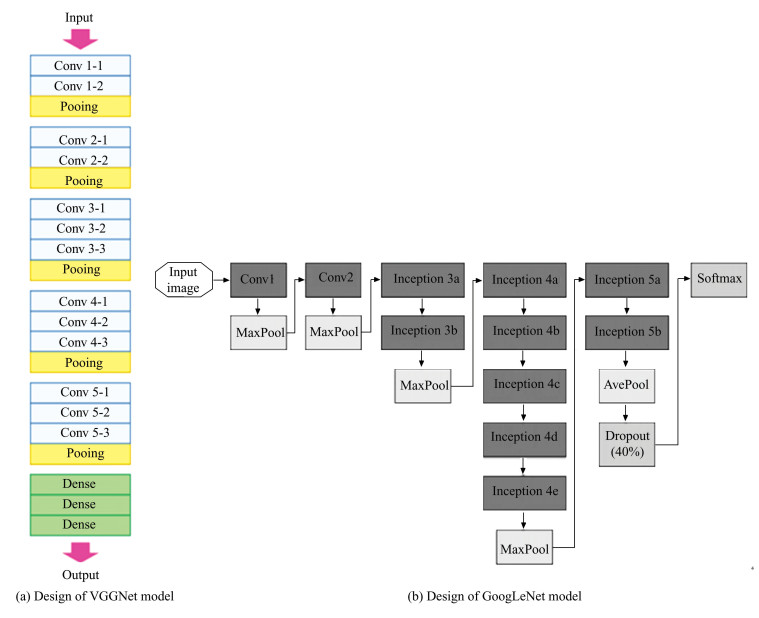
|
Fig.2 Design of the VGGNet model and GoogLeNet model for network forensics |
The output class from both these classifiers is evaluated via Eq. (15):
| $ \begin{equation*} C(\text { out })=\sum\limits_{i=1}^{N_{\mathrm{f}}} f(i) \cdot w(i)+b(i) \end{equation*} $ | (15) |
where, w and b are weights and biases, while f and Nf are feature values and number of features extracted by the DFO optimization process. These output classes are estimated for both VGGNet & GoogLeNet, and are given to binary cascaded neural networks, which utilize the complex architectures of both VGGNet and GoogLeNet to combine these models. Combining the feature maps from both models and running them through binary classifiers, which enable quicker computations by using binary weights and activations, are the two steps in the fusion process. This fusion-based approach aids in keeping or enhancing the accuracy of the system while reducing its complexity levels. The fused output class is represented via Eq.(16):
| $ \begin{equation*} c(\text { final })=A(\mathrm{VGG}) \times C(\mathrm{VGG})+A(G) \cdot C(G) \end{equation*} $ | (16) |
where, A and C represent testing accuracy, and output class from different classifiers. The advantages of VGGNet and GoogLeNet's complementary strengths are utilized by binary cascaded neural networks. While GooLeNet's parallel convolutional operations capture both local and global features, VGGNet's deep layers capture fine-grained details and complex patterns in the network traffic, enabling a more thorough analysis. These useful features are combined through the fusion process, improving the system's overall ability to detect anomalies and spot potential threats in network traffic scenarios.
There are several benefits to combining the VGGNet and GoogLeNet models using binary cascaded neural networks. By using binary weights and activations to simplify the computation, it first increases the effectiveness of analysis. As a result, network traffic data can be processed more quickly, making it suitable for real-time analysis in dynamic network environments. Second, the combination of these models improves anomaly detection's precision levels. The system can capture both intricate details and varied feature representations by combining the strengths of VGGNet and GoogLeNet, making it possible to identify anomalies and potential threats more precisely for different scenarios. Furthermore, by combining local and global features, the fusion technique offers a comprehensive view of network traffic patterns. This thorough analysis aids in locating sophisticated attack patterns that may involve various network scales and regions.
To overcome multiple mix attacks, we incorporated ensemble of VGGNet and GoogLeNet algorithms at forensic layer. Multiple-Mix-Attacks are characterized by their ability to incorporate several attack kinds and combinations, which makes them highly adaptable and difficult to defend against. Multiple-mix attacks can combine a few prevalent attack types. Examples of cybersecurity threats include distributed denial of service (DDoS) attacks, malware infections, phishing and social engineering, and insider threats. Attackers can utilize different mixes of these and other attack strategies to accomplish their goals, resulting in multiple-mix attacks that are highly dynamic and difficult to identify and counteract. Ensemble approaches may efficiently manage the complexity of multiple-mix attacks by combining various machine learning algorithms; each specialized in detecting specific attacks. The same has been highlighted in the paper.
Each model functions autonomously, examining distinct parts of the network and incoming data streams. Nevertheless, all of them contribute their forecasts to a centralized decision-making system, consolidating their results and reaching a conclusive verdict on whether an attack is taking place. Suppose the phishing email detection model identifies an email as suspicious, but the DDoS detection model does not simultaneously detect any abnormal network activity. In that case, the central system may prioritize conducting a thorough investigation of the email while monitoring the network for potential subsequent attacks. When the malware detection model identifies a dubious file on a network server, the central system takes immediate action. It isolates the affected system, prevents the spread of malware, and alerts human operators to conduct a comprehensive investigation into the incident.
To summarize, by utilising a combination of machine learning models specifically designed for various areas of cybersecurity, the financial institution can successfully protect itself against complex threats and ensure the security of its systems and data.Applications for the binary cascaded neural network-based fusion of the VGGNet and GoogLeNet models can be found in a variety of network security use cases. It can be used to improve the capabilities of intrusion detection and prevention systems by adding a forensic layer that tracks the origin of an attack, assesses the severity of the damage, and locates potential vulnerabilities for different scenarios. Administrators can proactively identify and mitigate emerging threats by using it for anomaly detection in network traffic monitoring scenarios. Efficiency of this model is evaluated in terms of different metrics on different datasets, and can be observed from the next section of this text.
1) Model selection criteria.
(1) Unique architectural features: The authors have chosen VGGNet and GoogLeNet, each with its own unique architectural features. VGGNet, known for its uniform architecture and deeper layers, is capable of capturing intricate details. On the other hand, GoogLeNet, with its inception modules, is designed to efficiently extract diverse features.
(2) Significance of performance metrics: The selection of VGGNet and GoogLeNet could have been influenced by key performance metrics such as accuracy, computational efficiency, and memory footprint. These models are renowned for their strong performance on image classification tasks, making them ideal for handling diverse attack patterns in cybersecurity.
(3) Advantages of pre-trained models: The availability of pre-trained models for VGGNet and GoogLeNet on large-scale image datasets like ImageNet can significantly speed up model development and fine-tuning. This allows for a quicker adaptation to the cybersecurity domain, saving valuable time and resources.
2) Optimization process.
(1) Training data preparation: Preparing training data for a cybersecurity model involves several crucial steps to ensure the model learns effectively and can generalize well to detect various cyber-attack types.
(2) Data collection: Identify and gather datasets representing different types of cyber-attacks. These datasets may include:
a. Intrusion detection datasets like NSL-KDD, UNSW-NB15, CICIDS 2017, etc.
b. Malware datasets containing samples of different malware families.
c. Phishing datasets containing examples of phishing emails or URLs.
d. Denial of Service (DoS) attack datasets.
e. Other relevant datasets are based on the specific focus of the model.
(3) Data labeling: Annotate the collected data with labels indicating whether each instance represents a regular activity or a specific type of cyber-attack. This step is crucial for supervised learning approaches.
(4) Data preprocessing: Clean the data to remove noise, inconsistencies, or irrelevant information. This may involve:
a. Handling missing values.
b. Removing duplicates.
c. Standardizing data formats.
(5) Feature engineering: Extract relevant features from the raw data to help the model distinguish between normal and malicious activities. This could include:
a. Extracting packet-level features from network traffic data.
b. Calculate statistical features from numerical data, like mean, standard deviation, etc.
c. Transforming categorical variables into numerical representations using techniques like one-hot encoding.
(6) Balancing the dataset: Ensure the dataset contains a balanced representation of normal and attack instances. Imbalanced datasets can lead to biased models, where the model may prioritize the majority class and perform poorly on minority classes.
3) Optimization techniques.
Dragonfly optimization uses a popular adaptive learning rate optimization algorithm that combines ideas from RMSProp and momentum. It adapts the learning rates for each parameter during training.
3 Result Analyses and ComparisonThe proposed model combines bio-inspired dragonfly optimization for identification of high-density feature sets. These feature sets are evaluated via use of combines Fourier transform, Z transform, laplace transform, DCT, 1D Haar wavelet, Gabor transform, and convolutional operations. The selected features are classified via a fusion of VGGNet & GoogLeNet models, which assist identification of different attack classes. These classes assist in forensic analysis via temporal evaluation of different attack types. The model was tested on the following datasets: UNSW dataset[22], cyber security datasets[23], network intrusion detection[24], BoT IoT datasets[25], leakage and forensics datasets[26].
These datasets were fused to form a total of 400 K data samples, out of which 60 K were used for validation, 280 K were used for training the model, while 60 K were used for testing the model under different attacks. These attacks include Sybil, Distributed Denial of Service (DDoS), Masquerading, Spoofing. These attack scenarios require the following parameters: precision (P), accuracy (A), recall (R), Area under the Curve (AUC), and delay levels. Precision measures the proportion of correctly identified attacks relative to the total number of instances categorized as attacks. It indicates the precision of the attack identification and is estimated using Eq. (17):
| $ \begin{equation*} P=\frac{\mathrm{TP}}{\mathrm{TP}+\mathrm{FP}} \end{equation*} $ | (17) |
where TP (True Positive) is the number of correctly identified attacks. FP (False Positive) is the number of non-attacks mistakenly identified as attacks.
Recall, also known as sensitivity or true positive rate, measures the proportion of correctly identified attacks out of all actual attacks. It indicates how well the method captures the attacks, and is estimated via Eq.(18):
| $ \begin{equation*} R=\frac{\mathrm{TP}}{\mathrm{TP}+\mathrm{FN}} \end{equation*} $ | (18) |
where FN (False Negative) is the number of attacks missed or not identified for different scenarios.
Accuracy measures the overall correctness of attack identification, considering both true positives and true negatives, which is estimated via Eq. (19):
| $\begin{equation*} A=\frac{\mathrm{TP}+\mathrm{TN}}{\mathrm{TP}+\mathrm{TN}+\mathrm{FP}+\mathrm{FN}} \end{equation*} $ | (19) |
where TN (True Negative) is the number of correctly identified non-attacks. The AUC is used to assess the performance of a binary classification model by plotting the Receiver Operating Characteristic (ROC) curve. It represents the area under this curve, which measures the model's ability to distinguish between attacks and non-attacks across different classification thresholds. Higher AUC values indicate better performance levels.
Based on this analysis, the precision levels were compared with BI[27], SCPD[28], & GNN[29], and can be observed in Fig. 3.
|
Fig.3 Levels of precision obtained during forensic analysis |
The proposed model outperforms BI [27], SCPD [28], and GNN [29] in terms of real-time attack detection precision by 4.5%, 5.5%, and 8.3%, respectively. These precision levels are enhanced by employing high-performance DFO-based feature selection and fusion of VGGNet & GoogLeNet, which allow for the extraction of probabilistic features and the accurate prediction of attack types for a wide range of network scenarios. Similarly, Fig. 4 depicts the accuracy achieved during these evaluations.
|
Fig.4 Levels of accuracy obtained during forensic analysis |
According to the results of this evaluation, it is clear that the proposed model improves the accuracy of attack detection in real-time by 4.5% in comparison to BI[27], 8.3% in comparison to SCPD[28], and 5.9% in comparison to GNN [29]. The implementation of the fusion of VGGNet and GoogleNet, as well as the extraction of multidomain features, both of which help with the accurate prediction of attack types for a variety of different network scenarios, contribute to an increase in these accuracy levels. Similarly, the recall obtained during these evaluations can be seen in Fig. 5.
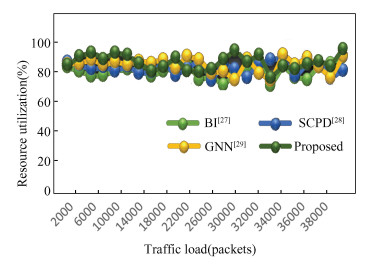
|
Fig.5 Levels of recall obtained during frorensic analysis |
This analysis shows that the proposed model has a better recall for attack detection in real-time scenarios than BI [27], SCPD[28], and GNN[29], by 8.3%, 9.4%, and 8.5%, respectively. To accurately predict attack types in different network scenarios, we fused VGGNet and GoogLeNet and used multidomain features to improve recall levels. Similarly, the AUC obtained during these evaluations can be seen in Fig. 6.
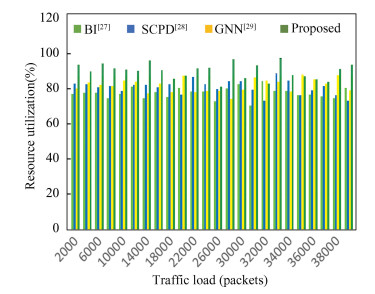
|
Fig.6 Levels of AUC obtained during forensic analysis |
According to the findings, the proposed model improves the AUC for detecting attack classes in real-time scenarios by 10.4% compared to BI [27], 12.4% compared to SCPD[28], and 8.5% compared to GNN[29]. This AUC can be improved, allowing for more precise prediction of attack classes across a broad spectrum of network traffic types, by combining multidomain features with high-performance fusion of VGGNet & GoogLeNet models and the use of DFO based feature selections. Similarly, the delay required for these evaluations is depicted in Fig. 7.

|
Fig.7 Levels of delay obtained during forensic analysis |
Based on the results, the proposed GNN[29] reduces the delay required to detect attack classes in real-time scenarios by 12.4% compared to BI[27], 10.5% compared to SCPD [28], and 12.9% compared to GNN[29]. By fusing high-performance VGGNet and GoogLeNet models with multidomain features and DFO-based feature selections, this delay is decreased. This improves the accuracy with which attack classes can be predicted across all forms of network traffic. These enhancements make the proposed model applicable to numerous ongoing forensic investigations & scenarios.
4 Conclusions and Future WorkThe design of an effective pre-forensic layer for preventing hybrid attacks through deep learning pattern analysis is presented in this paper. The proposed model seeks to decrease the necessary delay in real-time scenarios while increasing attack detection precision, accuracy, recall, and area under the curve (AUC).
The evaluations' findings unequivocally show that the proposed model outperforms other approaches such as BI, SCPD, and GNN. The proposed model outperforms BI, SCPD, and GNN in terms of attack detection precision by 4.5%, 5.5%, and 8.3%, respectively. This improvement is made possible by the integration of VGGNet and GoogLeNet and the use of high-performance feature selection based on DFO, which allows for the extraction of probabilistic features and the precise prediction of attack types in various network scenarios.
The proposed model also improves attack detection accuracy by 4.5% compared to BI, 8.3% compared to SCPD, and 5.9% compared to GNN. The model is able to make more accurate predictions of attack types in various network scenarios by fusing VGGNet and GoogLeNet and extracting multidomain features.
The evaluation results also show that, in terms of recall, the proposed model outperforms BI, SCPD, and GNN by 8.3%, 9.4%, and 8.5%, respectively. The combination of VGGNet and GoogLeNet, the extraction of multidomain features, and the precise prediction of attack types in various network scenarios are credited with this improvement.
The proposed model also performs better in terms of AUC, with a 10.4% increase compared to BI, a 12.4% increase compared to SCPD, and an 8.5% increase compared to GNN. The model achieves enhanced AUC, enabling more precise prediction of attack classes across a variety of network traffic types. This is made possible by the use of multidomain features, high-performance fusion of VGGNet and GoogLeNet models, and DFO-based feature selection.
The proposed GNN-based model reduces the time needed for identifying attack classes in real-time scenarios by 12.4% when compared to BI, 10.5% when compared to SCPD, and 12.9% when compared to GNN in terms of delay. By combining VGGNet and GoogLeNet models, multidomain features, and DFO-based feature selection, this reduction is made possible, leading to a more accurate and effective prediction of attack classes across various types of network traffic.
Overall, the optimizations suggested in this paper, such as the combination of VGGNet and GoogLeNet models, multidomain feature extraction, and DFO-based feature selection, show their efficacy in enhancing attack detection precision, accuracy, recall, and AUC, as well as in lowering the required delay in real-time forensic applications. The study's findings demonstrate the proposed model's applicability to a variety of real-time forensic situations, making a significant contribution to the field of network security and attack mitigations.
The paper offers a number of directions for additional study and advancement. Based on the results and ramifications of the current study, the following are some potential future scopes:
1) Improved model architecture: The performance of the suggested model can be enhanced by looking into deeper learning architectures further. To further improve attack detection precision, accuracy, recall, and AUC, researchers are looking into novel architectures like transformer-based models and graph neural networks.
2) Integration of new data sources: The current study concentrates on network traffic data, but adding new data sources, such as system logs, user behavior data, or endpoint telemetry, can give a more thorough understanding of hybrid attacks. The ability to detect attacks and conduct forensic analysis may be enhanced by integrating these various data sources and creating hybrid models that use multiple modalities.
3) Exploration of adversarial attacks: Network security systems are severely challenged by adversarial attacks. Future research on this topic could be interesting if it looked at how resilient the suggested model is to adversarial attacks and how to make it more resilient. To strengthen the model's defenses against evasion or poisoning attacks, one might consider adversarial training, defensive distillation, or the use of generative models.
4) Real-world deployment and evaluation: A thorough evaluation of the proposed model in various real-world network infrastructures and network environments will shed important light on its performance and practical applicability. The efficacy and generalizability of the model can be verified through extensive deployment trials and benchmarking against industry-standard datasets.
5) Managing uneven and changing data: Class imbalance in network traffic data, where specific attack types are underrepresented, is a common problem. The model's performance on rare attack classes can be enhanced by looking into methods to handle imbalanced data, such as oversampling, under sampling, or the use of advanced loss functions. For the model to be effective in the long run, techniques for adjusting it to changing attack patterns and dynamic network environments must also be developed.
6) Explainability and interpretability: Black boxes are frequently used to describe deep learning models. The goal of future research can be to make the suggested model easier to understand and interpret. To shed light on the model's decision-making process and increase credibility, strategies like attention mechanisms, saliency maps, or model-agnostic explanation methods can be used.
7) Deployment in edge and IoT devices: As edge computing and Internet of Things (IoT) devices proliferate, it is crucial to modify the suggested model for deployment in environments with limited resources. In distributed and IoT environments, real-time attack detection and forensic analysis are made possible by investigating techniques for model compression, quantization, and efficient inference.
Building cooperative defense systems that make use of the combined intelligence of numerous network components, such as routers, switches, and endpoints, can improve attack detection abilities. Exploring methods for collaborative information exchange between network devices, such as distributed learning, federated learning, or ensemble methods, can be a promising direction.
In summary, the paper's future work will focus on improving the suggested model, investigating new data sources, addressing adversarial attacks, carrying out real-world evaluations, handling imbalanced and evolving data, enhancing interpretability, deploying on edge and IoT devices, and creating collaborative defense systems. These guidelines can aid in the development of network security and make it easier to use deep learning-based forensic analysis in real-world situations.
| [1] |
Sathi V N, Murthy C S R. Distributed slice mobility attack: A novel targeted attack against network slices of 5G networks. IEEE Networking Letters, 2021, 3(1): 5-9. DOI:10.1109/LNET.2020.3044642 (  0) 0) |
| [2] |
Zhai Z, Lai G, Cheng B, et al. Lightweight secure detection service for malicious attacks in WSN with timestamp-based MAC. IEEE Transactions on Network and Service Management, 2022, 19(4): 5299-5311. DOI:10.1109/TNSM.2022.3194205 (  0) 0) |
| [3] |
Harada R, Shibata N, Kaneko S, et al. Quick suppression of DDoS attacks by frame priority control in IoT backhaul with construction of Mirai-based attacks. IEEE Access, 2022, 10: 22392-22399. DOI:10.1109/ACCESS.2022.3153067 (  0) 0) |
| [4] |
Park S, Kwon S, Park Y, et al. Session management for security systems in 5G standalone network. IEEE Access, 2022, 10: 73421-73436. DOI:10.1109/ACCESS.2022.3187053 (  0) 0) |
| [5] |
Nishanth N, Mujeeb A. Modeling and detection of flooding-based denial-of-service attack in wireless Ad Hoc network using Bayesian inference. IEEE Systems Journal, 2021, 15(1): 17-26. DOI:10.1109/JSYST.2020.2984797 (  0) 0) |
| [6] |
Pang Z-H, Fan L-Z, Dong Z, et al. False data injection attacks against partial sensor measurements of networked control systems. IEEE Transactions on Circuits and Systems Ⅱ: Express Briefs, 2022, 69(1): 149-153. DOI:10.1109/TCSⅡ.2021.3073724 (  0) 0) |
| [7] |
Stan O, Bitton R, Ezrets M, et al. , Extending attack graphs to represent cyber-attacks in communication protocols and modern IT networks. IEEE Transactions on Dependable and Secure Computing, 2022, 19(3): 1936-1954. DOI:10.1109/TDSC.2020.3041999 (  0) 0) |
| [8] |
Li Y, Zhao Y, Li J, et al. DDoS attack mitigation based on traffic scheduling in edge computing-enabled TWDM-PON. IEEE Access, 2021, 9: 166566-166578. DOI:10.1109/ACCESS.2021.3134671 (  0) 0) |
| [9] |
Nishanth N, Mujeeb A. Modeling and detection of flooding-based denial of service attacks in wireless Ad Hoc networks using uncertain reasoning. IEEE Transactions on Cognitive Communications and Networking, 2021, 7(3): 893-904. DOI:10.1109/TCCN.2021.3055503 (  0) 0) |
| [10] |
Zhang M, Wang L, Jajodia S, et al. Network attack surface: Lifting the concept of attack surface to the network level for evaluating networks' resilience against zero-day attacks. IEEE Transactions on Dependable and Secure Computing, 2021, 18(1): 310-324. DOI:10.1109/TDSC.2018.2889086 (  0) 0) |
| [11] |
Xiao S, Ge X, Han Q-L, et al. Secure distributed adaptive platooning control of automated vehicles over vehicular Ad-Hoc networks under denial-of-service attacks. IEEE Transactions on Cybernetics, 2022, 52(11): 12003-12015. DOI:10.1109/TCYB.2021.3074318 (  0) 0) |
| [12] |
Guo H, Sun J, Pang Z-H. Stealthy FDI attacks against networked control systems using two filters with an arbitrary gain. IEEE Transactions on Circuits and Systems Ⅱ: Express Briefs, 2022, 69(7): 3219-3223. DOI:10.1109/TCSⅡ.2022.3153481 (  0) 0) |
| [13] |
Fu Q-Y, Wang H-M. Detection of hijacking DDoS attack based on air interface traffic. IEEE Wireless Communications Letters, 2021, 10(10): 2225-2229. DOI:10.1109/LWC.2021.3097391 (  0) 0) |
| [14] |
Yang L, Wen C. Optimal jamming attack system against remote state estimation in wireless network control systems. IEEE Access, 2021, 9: 51679-51688. DOI:10.1109/ACCESS.2020.3046483 (  0) 0) |
| [15] |
Wang X, Ma X, Peng J, et al. On modeling link flooding attacks and defenses. IEEE Access, 2021, 9: 159198-159217. DOI:10.1109/ACCESS.2021.3131503 (  0) 0) |
| [16] |
Wu Z, Peng S, Liu L, et al. Detection of improved collusive interest flooding attacks using BO-GBM fusion algorithm in NDN. IEEE Transactions on Network Science and Engineering, 2023, 10(1): 239-252. DOI:10.1109/TNSE.2022.3206581 (  0) 0) |
| [17] |
Liu D, Ye D. Cluster synchronization of complex networks under denial-of-service attacks with distributed adaptive strategies. IEEE Transactions on Control of Network Systems, 2022, 9(1): 334-343. DOI:10.1109/TCNS.2021.3102012 (  0) 0) |
| [18] |
Gao Y, Xu M. Defense against software-defined network topology poisoning attacks. Tsinghua Science and Technology, 2023, 28(1): 39-46. DOI:10.26599/TST.2021.9010077 (  0) 0) |
| [19] |
Zhang M, Li G, Xu L, et al. Control plane reflection attacks and defenses in software-defined networks. IEEE/ACM Transactions on Networking, 2021, 29(2): 623-636. DOI:10.1109/TNET.2020.3040773 (  0) 0) |
| [20] |
Deng Y, Jiang H, Cai P, et al. Resource provisioning for mitigating edge DDoS attacks in MEC-enabled SDVN. IEEE Internet of Things Journal, 2022, 9(23): 24264-24280. DOI:10.1109/JIOT.2022.3189975 (  0) 0) |
| [21] |
Liu J, Labeau F. Detection of false data injection attacks in industrial wireless sensor networks exploiting network numerical sparsity. IEEE Transactions on Signal and Information Processing over Networks, 2021, 7: 676-688. DOI:10.1109/TSIPN.2021.3122289 (  0) 0) |
| [22] |
Kaggle. UNSW Dataset. https://www.kaggle.com/datasets/mrwellsdavid/unsw-nb15/download?datasetVersionNumber=1.
(  0) 0) |
| [23] |
Kaggle. Cyber-security datasets. https://www.kaggle.com/discussions/general/335189
(  0) 0) |
| [24] |
Kaggle. Network intrusion detection. https://www.kaggle.com/datasets/sampadab17/network-intrusion-detection.
(  0) 0) |
| [25] |
Kaggle. BoT IoT datasets. https://www.kaggle.com/datasets/vigneshvenkateswaran/bot-iot-5-data/download?datasetVersionNumber=1.
(  0) 0) |
| [26] |
Kaggle. Leakage and forensics datasets. https://www.kaggle.com/code/pietromaldini1/leakage-and-forensics.
(  0) 0) |
| [27] |
Pióro M, Mycek M, Tomaszewski A. Network protection against node attacks based on probabilistic availability measures. IEEE Transactions on Network and Service Management, 2021, 18(3): 2742-2763. DOI:10.1109/TNSM.2021.3067775 (  0) 0) |
| [28] |
Zhao L, Yuan H, Xu K, et al. Hybrid network attack prediction with Savitzky-Golay filter-assisted informer. Expert Systems with Applications, 2024, 235: 121126. DOI:10.1016/j.eswa.2023.121126 (  0) 0) |
| [29] |
Dai X, Lu H, Zhou W. Secure memory adaptive event-triggered filter design of nonlinear network system under hybrid network attacks with application to tunnel diode circuit. International Journal of Robust and Nonlinear Control, 2024, 34(8): 4999-5025. DOI:10.1002/rnc.7246 (  0) 0) |
 2024, Vol. 31
2024, Vol. 31


